Research & Publications
Research Projects
Blockchain Scalability
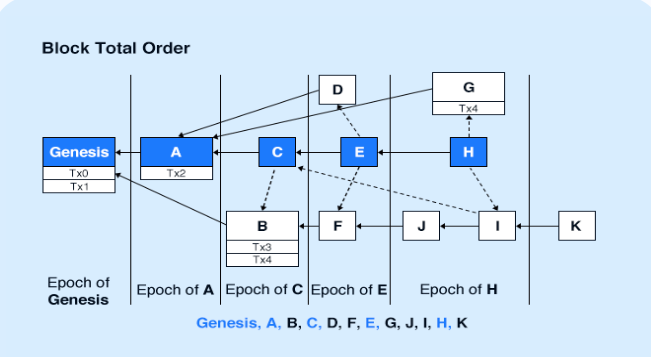
Following the success of the cryptocurrencies, blockchain has recently evolved into a technology platform that powers secure, decentralized, and consistent transaction ledgers at Internet-scale. However, the performance bottleneck remains one of the most critical challenges of current blockchains. In the standard Nakamoto consensus, the performance is bottlenecked by the facts 1) that only one participant can win the competition and contribute to the blockchain, i.e., concurrent blocks are discarded as forks, and 2) that the slowness is essential to defend against adversaries. For example, Bitcoin generates one 1MB block every 10 minutes and can therefore only process 7 transactions per second. The insufficient throughput and long confirmation delay severely limit the adoptions of blockchain techniques, causing poor user experience, congested network, and skyrocketing transaction fees.
Conflux
Conflux is a new fast, scalable, and decentralized blockchain system that can process thousands of transactions per second while confirming each transaction in minutes. Conflux records additional informations between blocks and organizes generated blocks into direct acyclic graphs. The core of Conflux is its consensus protocol that allows multiple participants to contribute to the Conflux blockchain concurrently (i.e., processing transactions in all concurrent blocks) while still being provably safe. See the Conflux project website for more information.
Shrec
Shrec is a novel transaction relay protocol for high-throughput blockchain systems built around a hybrid transaction hashing scheme that has a low hash collision rate, is resilient to collision attacks, and is fast to construct. Shrec reduces the bandwidth consumption by 60% at modest CPU overhead and improves the system throughput by up to 90%.
Gosig
Gosig is a scalable Byzantine consensus protocol for consortium blockchains. Gosig uses transmission pipelining to fully utilize the network bandwidth and uses aggregated signature gossip to reduce the number of messages. It can scale up to 5000 nodes while still maintaining the throughput of 3000 transactions per second.
Smart Contract Security
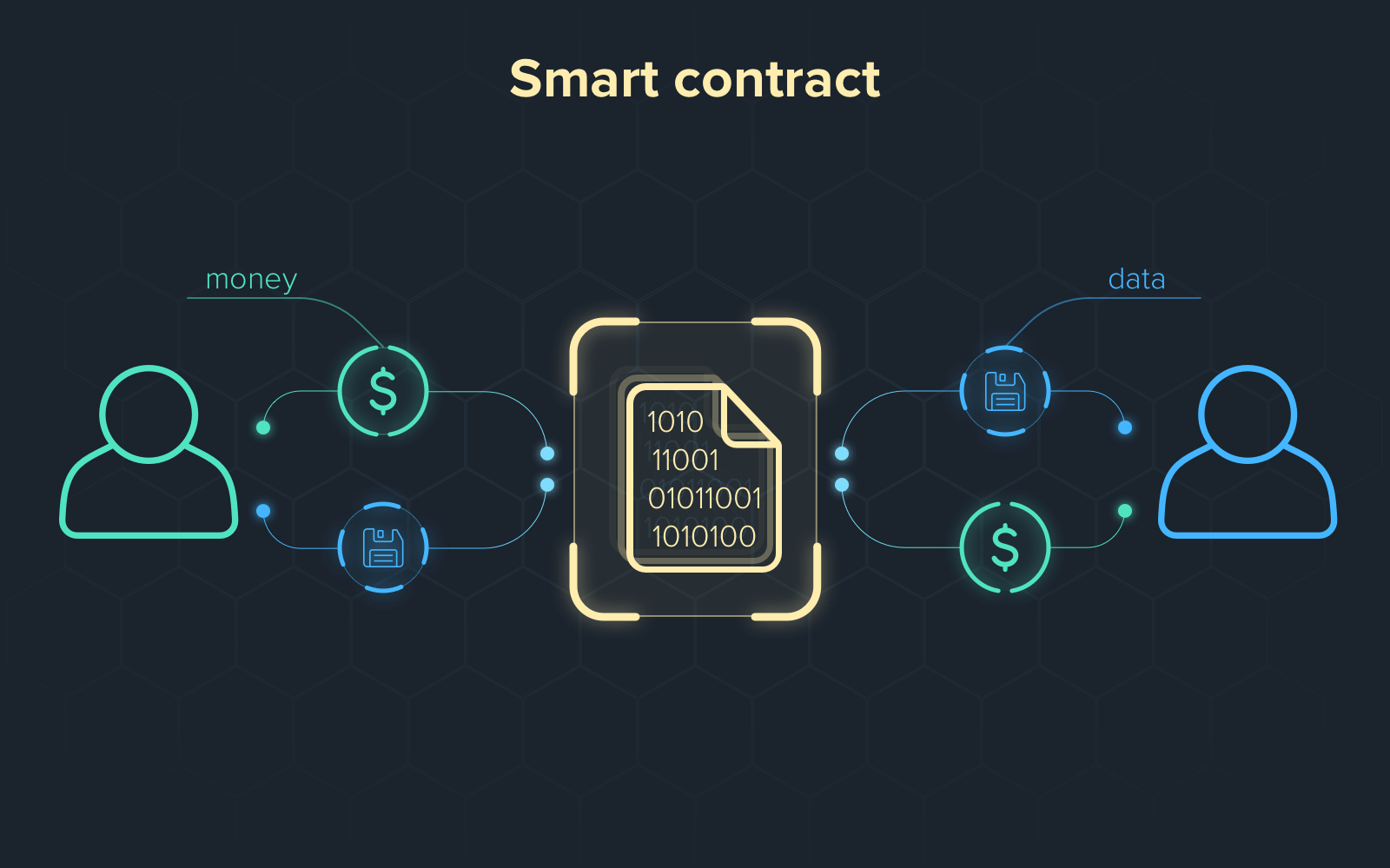
Smart contract is a program that encodes a set of transaction rules. Once deployed to a blockchain, its encoded rules are enforced by all participants of the blockchain network, and therefore it eliminates counterparty risks in sophisticated transactions. Unfortunately, like other programs, smart contracts may contain errors. Errors inside smart contracts often lead to significant financial losses in the real world.
Solythesis
Solythesis is a source-to-source runtime validation tool for Solidity. Its design is based on the observation that smart contract execution is not the performance bottleneck of blockchain systems. The overhead of runtime validation, which is often too expensive for other domains, is in fact negligible for smart contracts.

Automatic Patch Generation
Software defects are pervasive in software systems and can cause undesirable user experience, denial of service, or even security exploitation. Generating a patch for a defect is a tedious, time-consuming, and often repetitive process. Automatic patch generation techniques holds out the promise of automatically correcting software defects without the need for human developers to diagnose, understand, and correct these defects. To learn more, please visit our project website!
Prophet
Prophet is the state-of-art generate-and-validate patch generation system for C programs. It is the first system that uses machine learning techniques to learn from past successful human patches to recognize and predict correct patches for new errors.
SPR
SPR is the baseline system on which Prophet is built. It uses the condition synthesis technique to explore its search space up to two magnitude faster.
CodePhage
CodePhage systematically transfers useful security checks from a donor application to eliminate bugs and security vulnerabilities in a recipient application. It is the first system that transfers useful code across applications. It does not even require the source code of the donor application!
Input Filtering and Rectification
What if we cannot change the source code of an application? Let's look at the inputs of the application. We can make sure that malicious input cannot reach the application, i.e., filter them or rectify them.
SIFT
SIFT is a sound input filter system with sophisticated program analysis techniques. It guarantees to filter out all malicious inputs that trigger critical integer overflow errors. In practice, it also has zero to negligible false positives.
SOAP
SOAP is the first automatic input rectification system. It enforces a set of inferred invariants on the inputs so that potentially malicious inputs are transformed to benign inputs.

Program Recovery
What if an application crashes during its execution and we only have its binary? We can use our recovery shepherding technique to enable the application to survive the error triggering input unit and recovers its execution.
RCV
RCV is a lightweight program recovery tool with negligible overhead during normal execution. When a crash error (null-dereference and/or divide-by-zero) occurs, it systematically guides the application execution to survive the error triggering input unit. It also tracks how the error propagates in the application and waits until the error is flushed away after the program moves to the next input unit. Instead of crash and getting nothing, you can get part or all of your desired results.