Trackability
and Nimesha (Nim) Jayawardena
Background
Before diving into the meat of this report, it may help to review HTTP(S) and HTTP cookies.
HTTP
HTTP is an application layer protocol. Its purpose is to exchange resources between computers in a network.
So one computer could say, " GET me path/to/file.pdf," and the other computer responds with the requested file. Of course, GET isn't the only request method in HTTP — there are more:
- GET
- POST (to upload a new resource)
- PUT (to update an existing resource)
- DELETE
- HEAD, TRACE, OPTIONS, CONNECT, PATCH
HTTPS
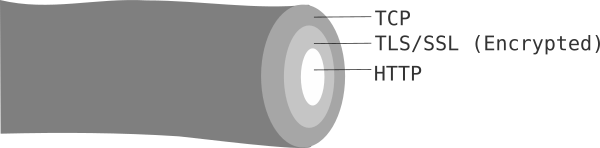
The transport layer protocol used by HTTP is TCP. HTTPS works the same except with an additional, encrypted layer in the middle called TLS (previously known as SSL).
HTTP Cookies
An HTTP cookie is a piece of information that is stored on the client's browser and included in the header of every HTTP request to a domain. They're typically used to keep site visitors "logged in". A cookie consists of a key (or "name") and a value (or "content"). A cookie may also contain some optional parameters such as an expiration date.
The server can create an HTTP cookie by including Set-Cookie: key=value in the header of an HTTP response. Once this response reaches the client, it is stored on the client's browser and sent inside every HTTP request to the same domain — until the cookie expires. If the expiration of the cookie was never specified, it will expire as soon as the browser is closed (i.e., when the "session" ends).

Note that HTTP cookies can also be created by the client. The client simply has to include the cookie in the header of the HTTP request.
Also note that cookies are domain-specific, so example.com couldn't access the cookies of peachytools.com. Even sub.example.com could not access the cookies of example.com (and vice-versa).
Zombie Cookies
A zombie cookie is a cookie that is recreated upon deletion. They are normally implemented by relying on another browser/HTTP API that provides some sort of local storage. A popular zombie cookies library called evercookie boasts to use more than 15 different techniques.
For a simple demonstration of zombies cookies, see our demo — or download the demo source code.
The demo makes use of a browser API called localStorage. localStorage is a JavaScript object with three methods that let you manage a domain-specific dictionary:
- getItem(key, value)
- setItem(key)
- removeItem(key)
You can learn more about localStorage here.
ISPs
Everyone is connected to the Internet by way of an Internet Service Provider, such as Bell or Verizon. Internet services providers, by their very nature, handle every data packet that enters or leaves your network. This gives them the unique opportunity to analyse what you do on the Internet and to even manipulate your Internet traffic.
In the US, as of 2017-03-28, Internet Service Providers are actually allowed to collect information about what website you visit and are then allowed to sell said info to advertisers. Additionally, many ISPs in the US have, in the past, redirected search queries through Paxfire to collect further information about a user's searches.
Super Cookies
A super cookie is a type of cookie that can track you across multiple domains. They can be in the form of anything from regular cookies whose origin is set to a top-level domain (such as .com) to a value injected by your ISP into your outbound requests.
Various Internet Service Providers have been caught injecting uniquely identifiable information into outbound requests. They can do this for two reasons:
- They sit between your network and the Internet and can thus modify all * your data packets
- Since you have to authenticate yourself to them, they can uniquely and consistently identify your network as the source of all data it sends
Verizon, for instance, injects a unique value that corresponds to your network into the headers of all HTTP requests you make. Receiving websites now only need to check the value that was set in the header to be able to uniquely identify you. Worse yet, since this value is the same for every request, they can even track you across domains.
*All unencrypted data anyway.
Fingerprinting
Fingerprinting (or browser fingerprinting) is a technique used to track visitors without the use of HTTP cookies. It's done by forming a unique "fingerprint" for the visitor using characteristics (e.g., operating system) provided to the server by your browser. Your browser exposes a ton of information about you. Here are just a few:
- operating system
- browser
- preferred language
- timezone offset
- supported fonts
- supported plugins
- hardware concurrency
- colour depth
- pixel ratio
You can explore the various information leaked by your browser and test the uniqueness of your fingerprint at Panopticlick.
Diversity and Stability
Of course, if you wanted to fingerprint your visitors, you wouldn't want to use all features available to you. An ideal set of features is both diverse and stable. Diverse features are those that can take on many different values and vary from user to user (e.g., list of supported fonts). Stable features are those that do not change over time (e.g., operating system).
Canvas Fingerprinting
This is a concept first introduced in a paper published in 2012. It works by rendering some text on an HTML5 canvas, and reading the canvas pixel-by-pixel. The key lies in the fact that text is rendered differently on various machines.
This rendering is dependent on your operating system, browser, GPU, and graphics card — so canvas fingerprints can be quite diverse. Of course, you're not limited to just text; you might have better luck rendering complex graphics.

Demo
If you're intrested in playing around with browser fingerprinting, you can download our PHP demo. It employs a library called fingerprintjs2 to track visitors. To configure the features used for the fingerprint, see js/fingerprint.js.
Defense
There are various ways you can try to defend yourself from tracking, each with various downsides and levels of effectiveness. We describe some of the methods of defense below.
Disable JavaScript
Not the most effective defense. Very painful to do, lots of websites use JavaScript.
| Zombie Cookies | Works for this! |
| Super Cookies | Has no effect on most forms of super cookies. |
| Fingerprinting | Can prevent some forms of fingerprinting. It cannot block all indentifiable information, however. Your user-agent, for instance, would be unaffected by this. In fact, this would probably make you more fingerprintable. After all, how many people return the same indentifiable information you do but also have JavaScript disabled? Probably even less. |
| Snooping | Has no effect on snooping. |
| ISP Redirect | Has no effect on malicious redirects by your ISP, such as Paxfire. |
HTTPS
HTTPS is definitely the most convenient defense here. However, it is not the most effective.
Encrypts HTTP traffic between you and a website and ensures its integrity.
| Zombie Cookies | Has no effect on zombie cookies. |
| Super Cookies | Can prevent some super cookies, such as those that take the form of data injection by an ISP. It will not prevent all super cookies, however. |
| Fingerprinting | Has no effect on fingerprinting. |
| Snooping | While this does prevent ISPs from seeing the contents of HTTP packets, they can still see where packets are destined to. That is, they still know what websites you visit. |
| ISP Redirect | This does not prevent malicious redirects by your ISP. Unless you explicitly type in https:// before the website you visit, an ISP can either redirect to a different domain that uses HTTPS or return fake results and hope you do not notice that it is not HTTPS. |
HTTPS + HSTS
Just as convenient as HTTPS, but more secure.
Like HTTPS, but tells your browser to always except HTTPS at some domain.
| Zombie Cookies | Has no effect on zombie cookies. |
| Super Cookies | Can prevent some super cookies, such as those that take the form of data injection by an ISP. It will not prevent all super cookies, however. |
| Fingerprinting | Has no effect on fingerprinting. |
| Snooping | While this does prevent ISPs from seeing the contents of HTTP packets, they can still see where packets are destined to. That is, they still know what websites you visit. |
| ISP Redirect | Works for this! |
VPN
Somewhat convenient. Not the most effective.
Sends data through another server, the VPN server. Both your computer and the VPN server authenticate each other and create an encrypted channel between each other. This ensures all data being routed through your VPN is reaching your VPN server without being seen or touched by anyone else. Your VPN server then makes the request just as your computer normally would.
Note, this is not necessarily true for all VPNs. This section is heavily based on OpenVPNs implementation. Some VPN protocols are merely dumb proxies which offer no extra security.
| Zombie Cookies | Has no effect on zombie cookies. |
| Super Cookies | Can prevent your ISP from injecting super cookies into requests. However, now your VPN provider and its ISP is in the position of your normal ISP. That is, they could inject super cookies instead. Further, this does not prevent other types of super cookies. |
| Fingerprinting | Has no effect on fingerprinting. |
| Snooping | Can prevent your ISP from snooping. However, now your VPN provider and its ISP is in the position of your normal ISP. That is, they could snoop on your traffic instead. |
| ISP Redirect | Can prevent your ISP maliciously redirecting you. However, now your VPN provider and its ISP is in the position of your normal ISP. That is, they could maliciously redirect you instead. |
Tor
Even less convenient, but more effective.
Works by using encryption to route your traffic through several servers, with each server only knowing previous and next server in the chain. Essentially masks where traffic is coming from.
| Zombie Cookies | Has no effect on zombie cookies. |
| Super Cookies | Prevents ISPs from injecting values into requests. Does not prevent other forms of super cookies, such as TLD origin cookies, however. |
| Fingerprinting | Has no effect on fingerprinting. |
| Snooping | Works for this! |
| ISP Redirect | Works for this! |
Tails
Least convenient. Most secure.
Tails is an amnesiac operating system with a focus on privacy and security. Tails ensures all traffic is sent through Tor, zombie cookies are blocked, the most common screen resolution is given to websites, canvas fingerprinting is blocked, etc.
Further, everything you do on Tails is erased when your turn off your computer, ensuring you cannot be tracked between sessions. It even goes as far as writing over memory several times on poweroff to ensure you cannot be the victim of a coldboot attack.
| Zombie Cookies | Works for this! |
| Super Cookies | Works for this! |
| Fingerprinting | Works for this! |
| Snooping | Works for this! |
| ISP Redirects | Works for this! |