Using apktool and dex2jar found in the kali linux distribution.

Reverse Engineering is the process of taking a built product and deassembling it into its building pieces. We are going to talk about reverse engineering android apps specifically.
When you click on build on Android studio, it creates an apk file. An apk file is simply an archive named with .apk extension. So whats inside this apk? If you take the apk and unzip it, you get something like the follwing:
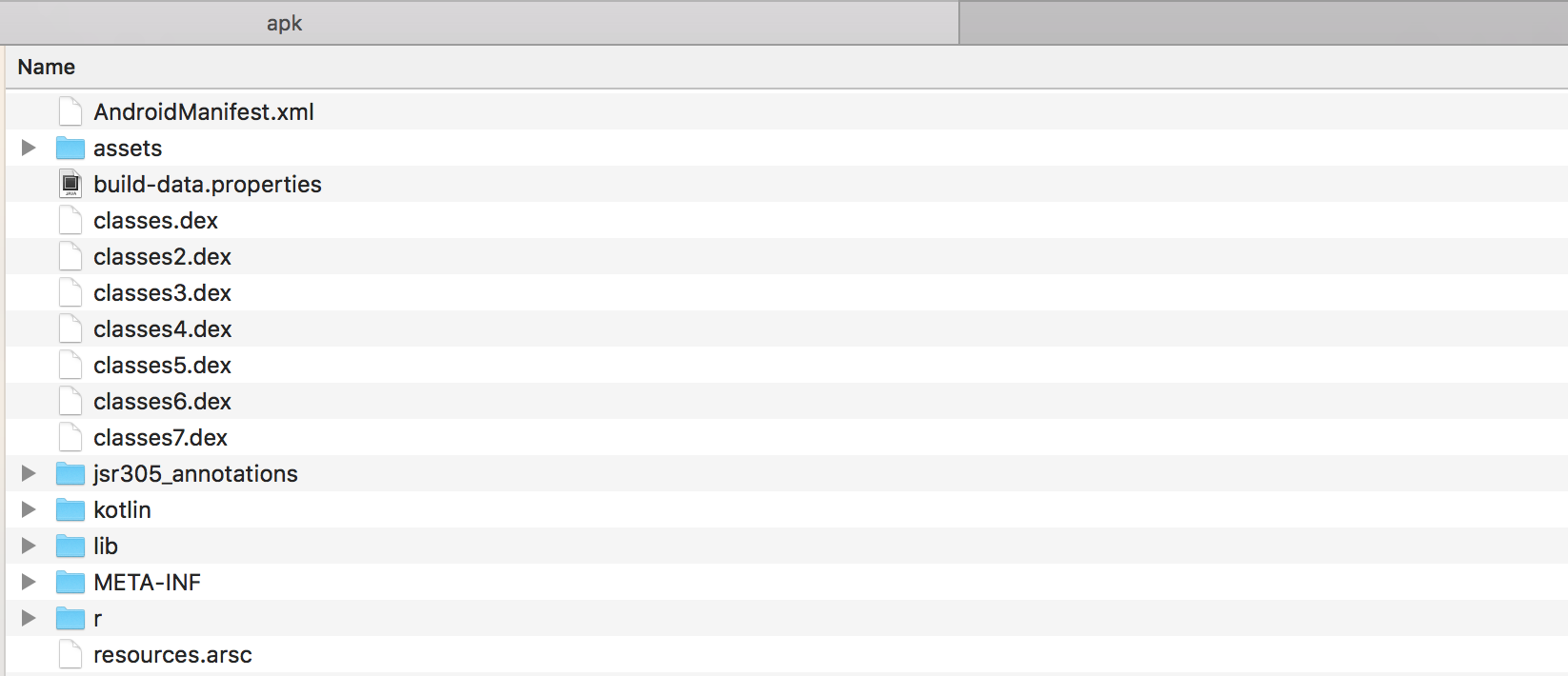
We have the Android Manifest, classes.dex, library and resources. All these files and folders make the final app. The following image describes each one briefly:
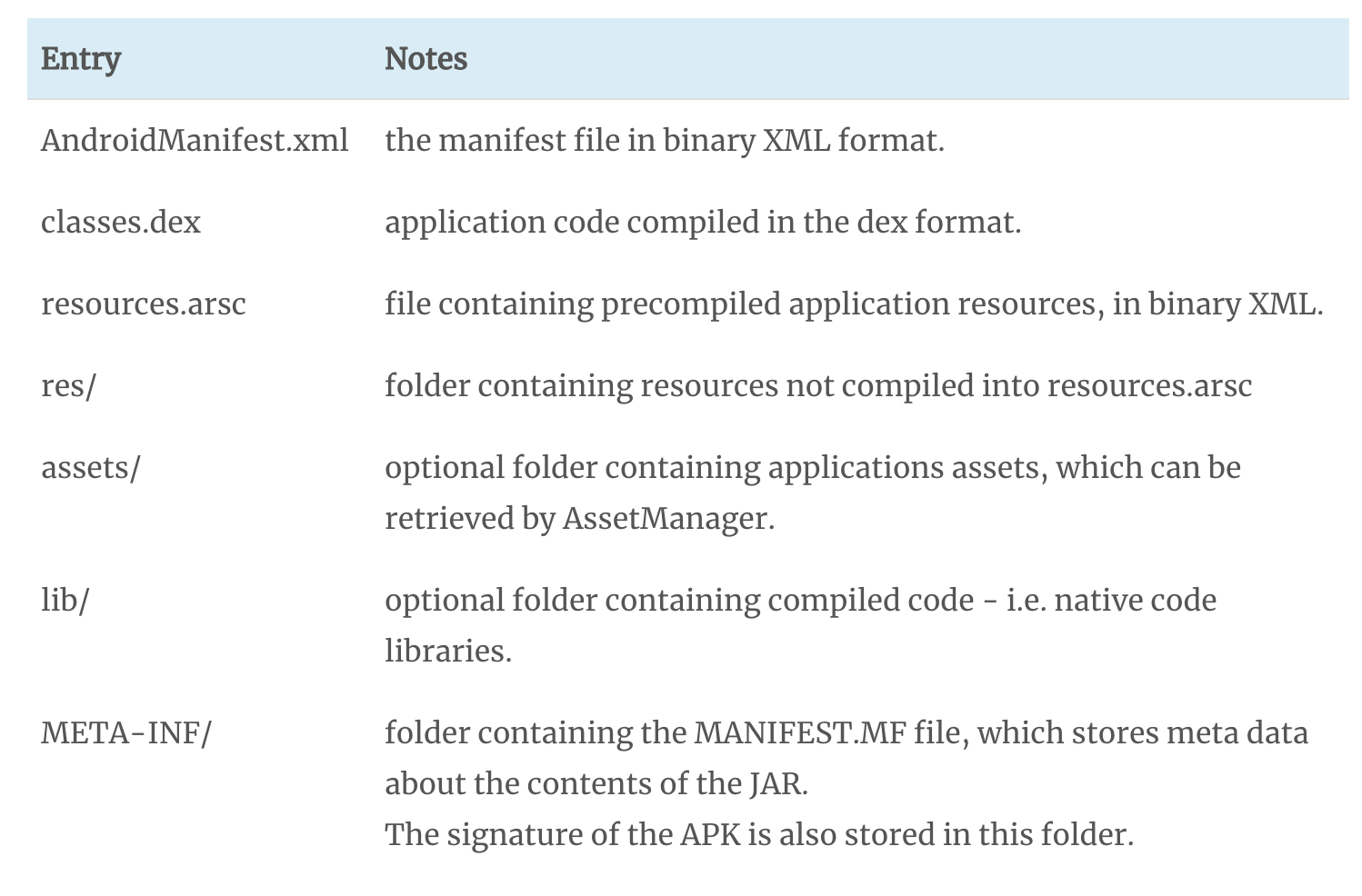
Ok so the imporant stuff are the xml files and .dex files. However these files are non human readable, the xml files are in binary format and the source code is in bytecode. So this is where reverse engineering will come in handy. Lets discuss dex files before moving on.
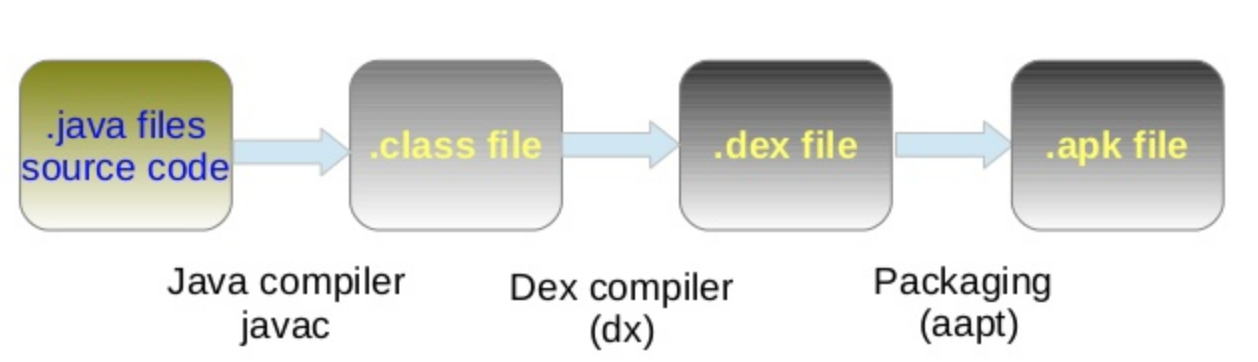
.dex files contain all the source code (all .java source files) in compiled bytecode. To understand better, see the following image:
This tool has two uses: Build and Decode. Basically build an apk and decode an apk.
Example of command: apk-tool d app.apk
Decoding the .dex into a more human readable format (.smali) as well as converting binary XML to human readable text. It takes the .dex files (android bytecode) and disassemble them into their assembly format (.smali files).
It uses the Smali package to disassemble the dex files. Smali is an assembly language for dalvik bytecode (.dex files).
We can modify the XML files to make very high level changes such as change colours of the app UI, change app title and text strings used within app. We can change the core logic of the app by modifying the smali files which contain the algorithms/source code of app.
Example of command: apk-tool b app
Takes your modified files from reverse engineered apk and repackages it into an apk archive.
It uses the Smali package to take all the smali files and assemble them into .dex dalvik bytecode. Will convert the XML to binary format and create the packaged apk inside your apk folder/dist.
This tool is similar to apktool in that it deconstructs bytecode into a more human readable format. It just does it in a different way.
The mitigation we're going to go over mostly involves hiding important strings from malicious activity.
Strings are vulnerable in binaries because you can use the Unix strings utility to grab them
It was once thought that hiding strings in environment variables would prevent them from being found out, but the gradle build process simply put those enviroment variables in a separate BuildConfig class. No mitigation achieved at all.
Proguard is an open source utility made by GuardSquare to optimize and obfuscate android code.
However, this doesn't mitigate against the strings utlity but it does make identification of code that holds important strings pretty difficult. The obfuscation process simply replaces class and method names with useless names, but a skilled reverse engineer could manage to understand some fo the logic behind the application.
The native development kit compiles code down into .so files. The code within these .so files can be disassembled, but the reverse engineering of this assembly code is orders of magnitude more difficult.
This process also doesn't mitigate against the Unix Strings utility.
DexGuard is the enterprise grade sibling of Proguard, and it optimizes, obfuscates and encrypts all components of the app.
It goes so far as to encrypt and obfuscate strings, arithmetic/logical expressions, and control flow.
There's always the option of building a custom solution where you expose little to nothing on the client side and then interface with a custom backend REST API that you fully control. To secure access to this backend you would need to establish trust via a public/private key exchange.