Cain and Abel
Contents
- Introduction
- Features
- Main Features
- Other Features
- Local Passwords
- LSA Secret
- Wireless password
- IE 7-9 Auto Forms Passwords
- LM(Lan Manager hash) and NTLM
- Cracking with Cain
- Bruteforce
- Dictionary
- Rainbow tables
- Address Resolution Protocol
- ARP Poisoning Routing
- Overview
- Sniffing the network
- Bypassing HTTPS
- Result
- Defenses
- Against Cracker
- Against ARP poisoning
- Disadvantages of Cain
- Demo
- Decoder
- Cracker
- ARP
- Sources
1. Introduction
Cain and Abel is a password recovery tool. It is very broad, that is it does not get passwords in only one way but utilizes many possible attacks to get the password of a system. It is exclusive to Windows and can’t be ran on Linux and OSX. It is typically used by attackers who wish to gain unauthorized access to a system, but can be used by a defender when an attacker locks them out of their system or to test the strengths of their defenses.
2. Features
2.1 Main Features
These are the features that we chose to talk about in the presentation. These are the features that Cain and Abel is typically used for.
- Finding and cracking stored passwords
- Cracking password hashes using bruteforce, dictionary, or rainbow table attacks
- Enumerating and sniffing the network
- Attacking via ARP Poisoning
2.2 Other Features
There are many other features that Cain and Abel have, some of which are outdated (like the Dialup password cracker) or ones that are not as widely used as the main features. To see the full list of features that it offers you can visit this site: http://resources.infosecinstitute.com/password-cracking-using-cain-abel/
3. Local Passwords
3.1 LSA Secret
- Stored in registry at HKEY_LOCAL_MACHINE/Security/Policy/Secrets
- This is used for managing a system's local security policy, auditing, authenticating, logging users on to the system, and storing private data.
- Default Password: passwords used to logon to Windows if auto-logon is enabled
- DPAPI: IE passwords are protected using DPAPI and login URL as entropy before saved in the registry.
3.2 Wireless password
- Stored in registry for Windows XP; stored as local files(.xml) for Vista and above.
- The password is encrypted but Cain can decrypt the password and present in plain text format.
3.3 IE 7-9 Auto Forms Passwords
- The hash of the website link is stored in registry. This hash can be brute-forced by using IE history to get plain text version of website link.
- The username/password information is encrypted using DPAPI and stored.
- Decrypting username/password information can simply be done with Windows cryptography functions.
3.4 LM(Lan Manager hash) and NTLM
- LM/NTLM are suite of Microsoft security protocols that provides authentication, integrity, and confidentiality to users.
- They are stored in c:\windows\system32\config\SAM. The file is encrypted and locked when Windows is running, but Cain can bypass the lock and decrypt the SAM file to get LM/NTLM hashes.
- LM/NTLM hashes are used for local logon.
- LTLM hash is introduced in 1993 with Windows NT 3.1 to replace LM hash.
- LM is based on DES but is broken due to its design flaws. First, LM hash only supports up to 14 characters. Second, passwords longer than 7 characters are divided and hashed separately. Third, the password is converted into all uppercase letters in the first process of LM hash. As a result, the key-space of LM hash is only 69^7; brute-force attack can crack the hash in few hours.
- NTLM is based on MD4 and does not have maximum length limitation. Therefore, NTLM is much secure than LM hashes. However, Windows does not utilize a technique called salting. As a result, NTLM hashes stored in Windows are vulnerable to rainbow table attacks.
- Refer to http://www.windowsecurity.com/articles-tutorials/authentication_and_encryption/How-Cracked-Windows-Password-Part1.html for further information on LM and NTLM hashes.
4. Cracking with Cain
4.1 Bruteforce
- Bruteforce is a relatively simple attack which tries every single possible password combination based on password length as well as what the password may consist of.
- In Cain and Abel you are able to specify the minimum length of the password, the maximum length, and the character set that it may consist of (like alphanumeric, special symbols, etc)
- The way bruteforcing works in Cain in Abel is as follows. First a hash that the user wants to crack is specified. Then once the attack is initiated, some permutation of the character set is hashed using the hash function through which the data we’re trying to crack was hashed. Then the result of that is compared to our original hash. If it matches, that means we have found the plaintext password. Otherwise another permutation is tried.
4.2 Dictionary Attack
- Dictionary attacks are used when a bruteforce attack would take far too much time. It tries to gain access to a system by trying a list of pre-determined passwords, most of the time the most commonly used password. So it would try passwords like “password”,”letmein”,”p4ssw0rd”, and so on. This list of passwords, typically stored as a text file, is called a dictionary.
- Cain and Abel does not come with a dictionary pre-installed, so you have to find one on your own. In our demonstrations we used a dictionary which contained the 10,000 most used passwords which you can find at https://github.com/discourse/discourse/blob/master/lib/common_passwords/10k-common-passwords.txt
- Cain and Abel also allows for password mangling. What this means is that there are several checkboxes which allow you to change or “mangle” the dictionary. For example if you checked the option for numerical replacement, if you had a word like “password” in your dictionary file it would also try “p4ssword”,”passw0rd”,”p455word” and so on. Depending on the size of your dictionary file it may slow down the attack as you’re trying more combinations, but it is unlikely to matter as dictionary attacks tend to be quite fast.
- The way it works is similar to bruteforcing. The password is hashed, and the hashes are compared.
- Statistically speaking you can gain access to up to 91% of accounts by trying only the top 1,000 passwords. This lack of creativity in users is why dictionary attacks are so potent.
4.2 Rainbow Table Attack
- A rainbow table is precomputed table used for cracking hashes.
- It is an example of a space/time trade-off. Rainbow table uses less computer processing time and more storage than a brute-force attack, but uses more processing time and less storage than a simple lookup table.
- A simple lookup table that contains one entry per hash would use too much storage. So rainbow table uses a technique called precomputed hash chains to use less storage. This technique requires to define a reduction function R that maps hash values back into some values in finite set of passwords. By alternating the hash function with the reduction function, a chain is formed.
- To generate a rainbow table, a set of initial passwords and a fixed chain length k for each initial passwords are defined, and hash chains are computed. Then only the first and last password in each chain is stored into rainbow table.
- Given a hash function H, and a reduction function R, this is an example of a chain:
![\mathbf{aaaaaa}\,\xrightarrow[\;H\;]{}\,\mathrm{281DAF40}\,\xrightarrow[\;R\;]{}\,\mathrm{sgfnyd}\,\xrightarrow[\;H\;]{}\,\mathrm{920ECF10}\,\xrightarrow[\;R\;]{}\,\mathbf{kiebgt}](images/image05.png)
- In the above case, the initial password is “aaaaaa” and the last password is “kiebgt”. Only these two values would be stored into the rainbow table.
- Now, if one would crack a hash “281DAF40” using rainbow table, he can alternate between the reduction function and the hash function until he sees a password in the endpoint. In this case, R(H(R(H(“281DAF40”)))) would be “kiebgt”. The initial password is “aaaaaa” in that chain, and can regenerate the chain to figure out which password in the chain hashes to “281DAF40”; in this case would be just “aaaaaa”, and the password is found.
- Note that the hash may not be found the the chain. For example a hash value “FB107E70” may become “kiebgt” even though it’s not in the chain starting at “aaaaaa”. This is called a false alarm, and simply ignored and continues to extend the chain. If chain is extended to length k, maximum chain length, with no good matches, then the chain that contains the password that produces the hash value was never computed when creating the rainbow table.
- There exists few problems with simple hash chains. For example collision handling is very hard, and choosing effective reduction function R is also very hard. Rainbow table solves this problem by using sequence of reduction functions R_1 through R_k. A collision must happen on the same iteration in order for margins to happen. This also changes how the lookup is done: generate k different chains that assumes the hash value is in the last position, second to last position, and so on until the last chain.
5. Address Resolution Protocol (ARP)
- Address Resolution Protocol(ARP) is a protocol used for resolution of network layer addresses into link layer addresses. ARP protocol is used within the Local Area Network(LAN) in order to convert an IP address to a MAC address.
- ARP uses a message format that either contains address resolution request or response.
- ARP request: A request to find out which host has the specified IP address. It is a broadcast; therefore, all the hosts in the same LAN will receive the request. The host that has the specified IP address responds back to the sender of ARP request while others discard the packet silently.
- ARP response: A response contains the IP address and MAC address of the current host. ARP response is sent back only to the sender of ARP request that asked for the current host’s IP address.
- ARP cache: a stored mapping of IP addresses with MAC addresses. This cache is used to reduce the number of ARP requests or responses. The ARP cache is periodically flushed to delete unused entries.
- ARP announcements: ARP can be used as an announcement protocol. The announcement is used for updating other hosts mapping of a hardware address when the sender’s IP address or MAC address has changed. ARP announcement updates any cached entries in the ARP tables of other hosts that receive the packet.
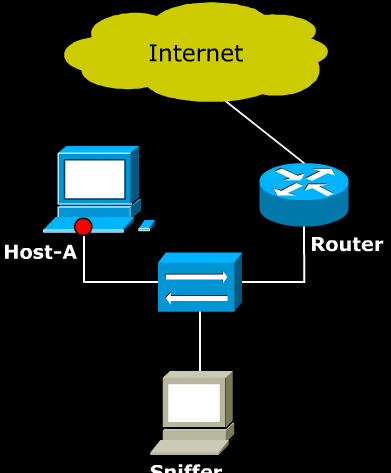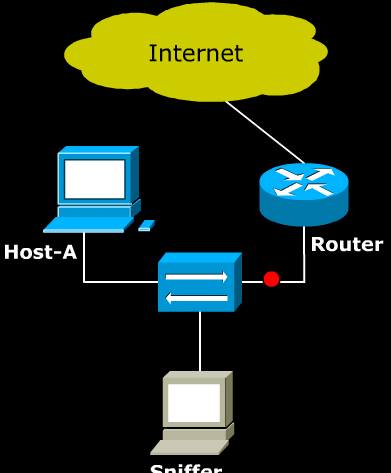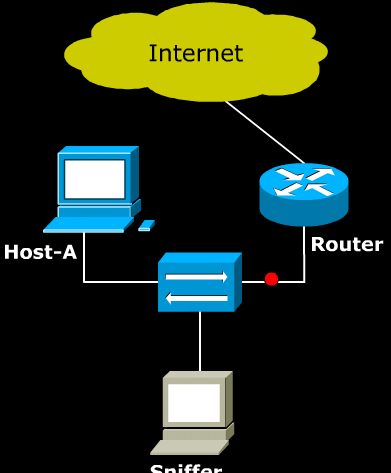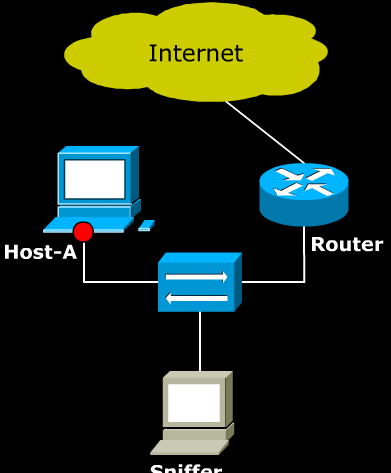
- The above image shows how ARP cache can be used to communicate between two hosts. Host-A can find Host-B’s MAC address in its ARP cache and therefore can send traffic to Host-B.
6. ARP Poisoning Routing
6.1 Overview
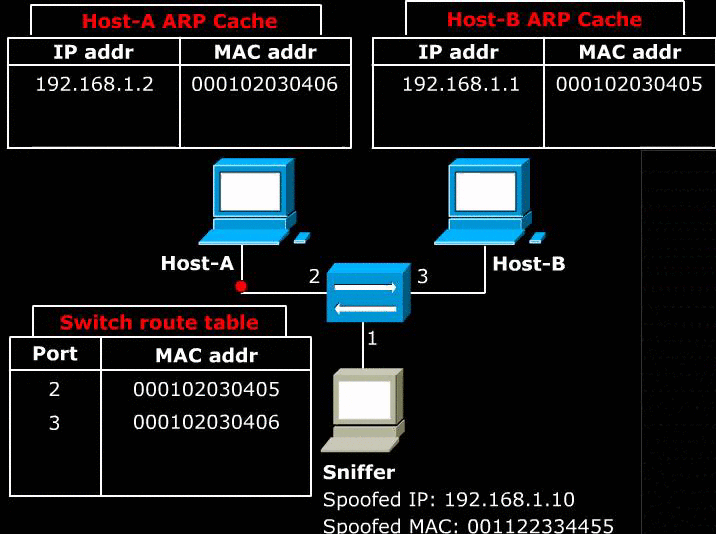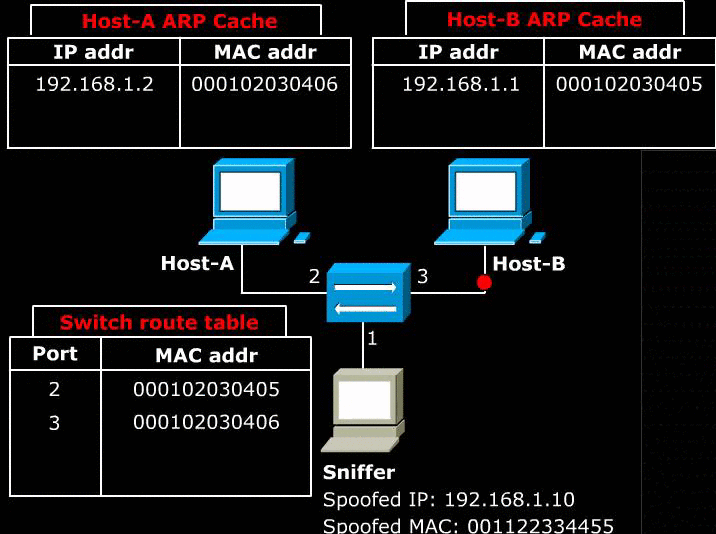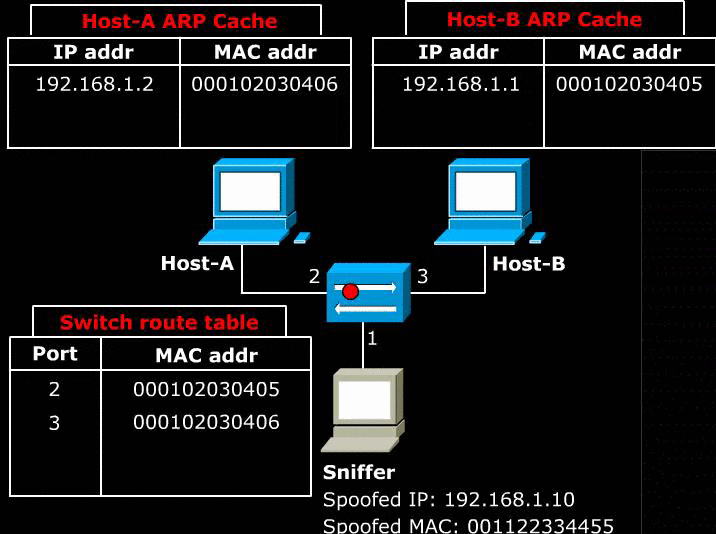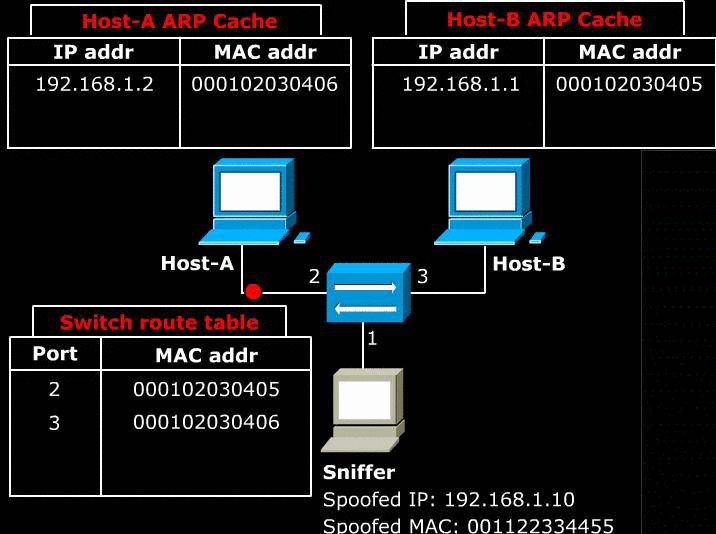
- As explained in section 5, ARP protocol is used within the Local Area Network. The problem is that LAN is designed without any sort of authentication technology. As a result, any host in the LAN can impersonate another host, and can reroute all of the LAN’s traffic through itself. The impersonation can be done by use of ARP announcement.
-
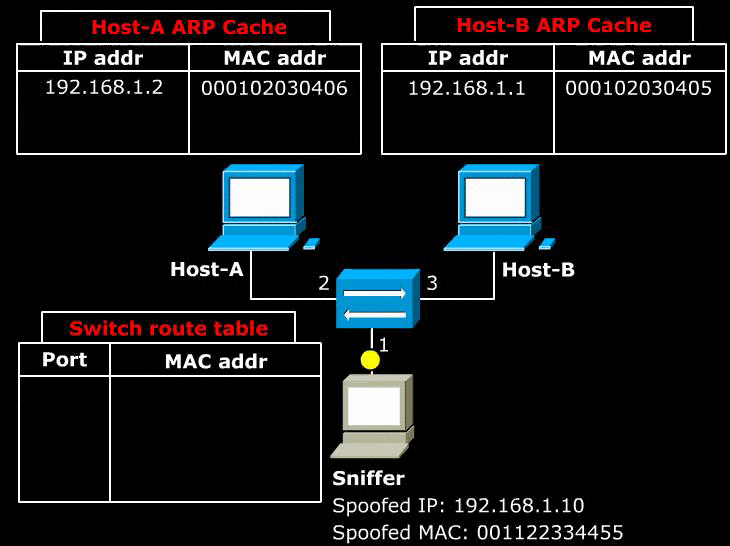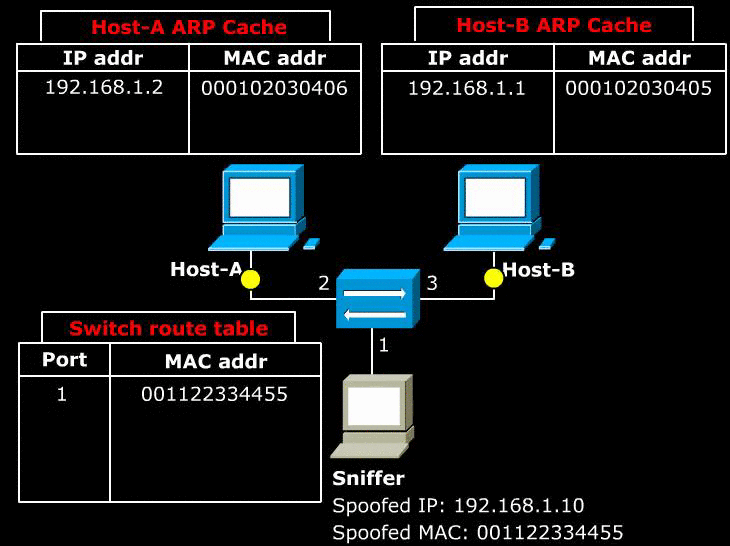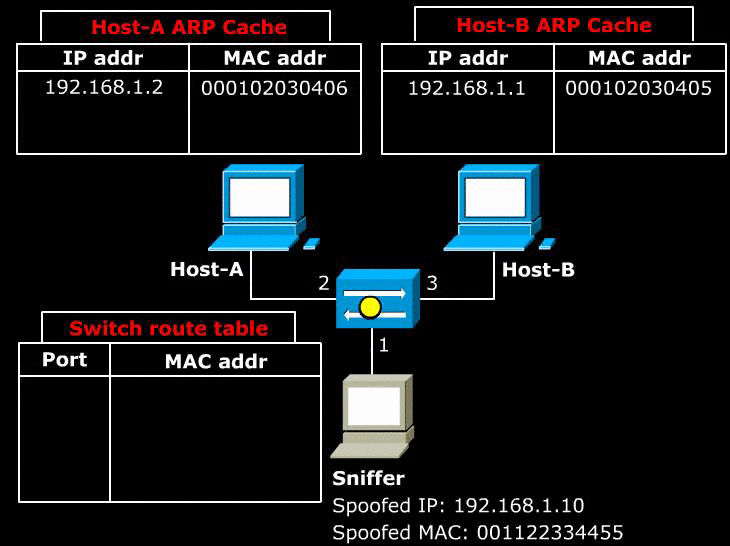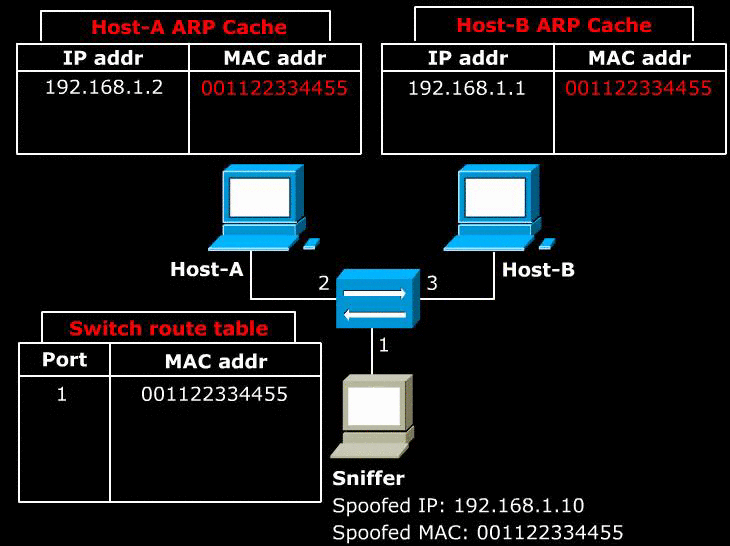
- Above image shows a Sniffer sends a malicious ARP announcement to two target hosts. The packet tells Host-A that Host-B can be found at the MAC 001122334455. It also tells Host-B that Host-A can be found at the MAC 001122334455.
- Note that because the ARP cache is is periodically flushed to delete unused entries, Sniffer needs to continuously send this ARP announcement at regular intervals.
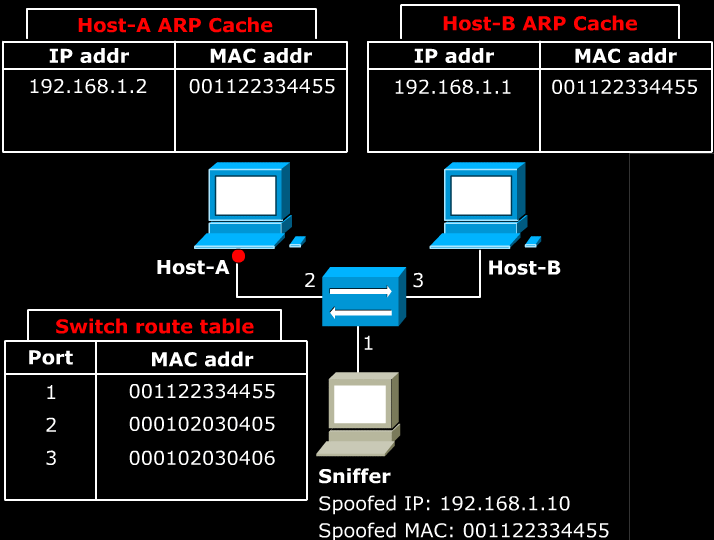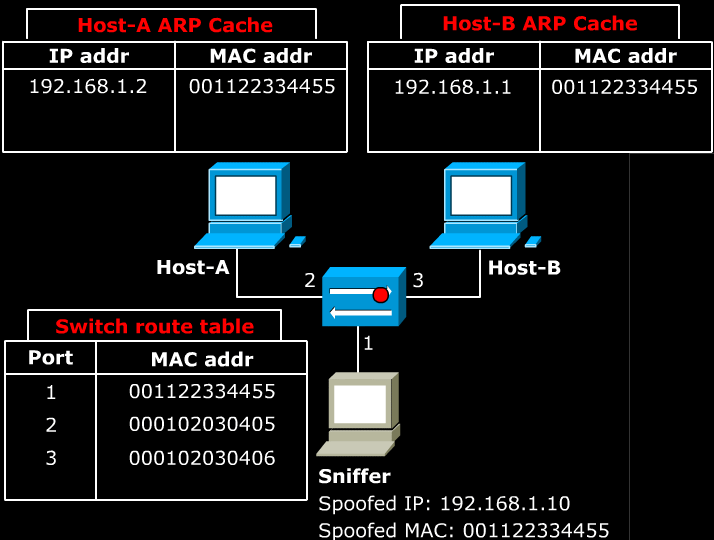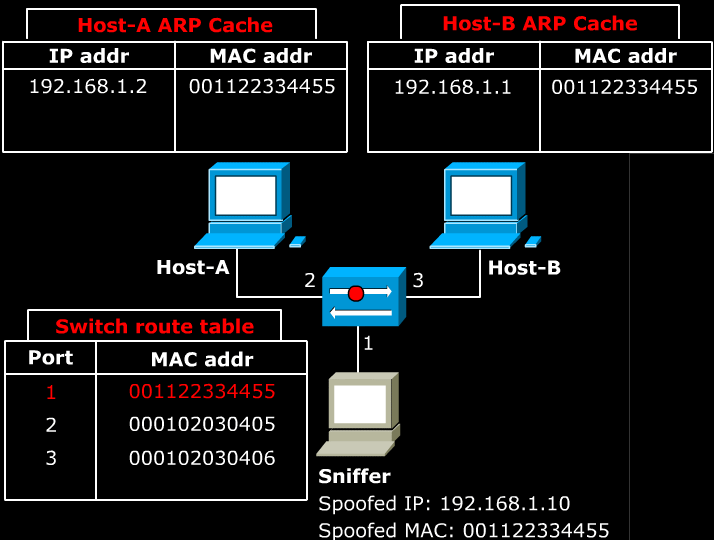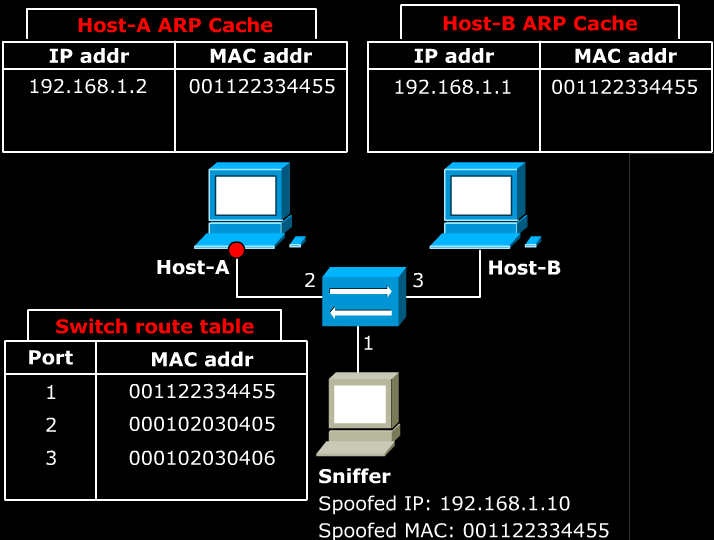
- As a result, any packet that is sent between Host-A and Host-B first sent to the Sniffer. The Sniffer can simply re-route the packets to correct destination to act as a man in the middle. If the Sniffer simply discards the packets, it would cause a Denial of Service.
6.1 Sniffing the network
- ARP protocol is used within the Local Area Network. Therefore, ARP poisoning cannot be used to make the host in the external LAN to send packets to the Sniffer. However, there is a way around it which is to impersonate the Router.
- Above image shows what happens when Host-A and Router is poisoned. The sniffer can sniff all the traffic between Host-A and Router which is connected to external network(Internet).
6.2 Bypassing HTTPS
- Nowadays, secure websites communicate with the host through HTTPS protocol. HTTPS is communication protocol for secure communication. This is done by layering HTTP on top of SSL or TLS protocol.
- SSL/TLS are cryptographic protocols that use X.509 certificates to provide communication security. During the handshake process between client and server, the client receives a digital certificate from the server which contains the server name, the trusted certificate authority(CA), and the server’s public encryption key. Then the client can encrypt messages using public key such that only the server that has private key can decrypt. SSL/TLS, thus, provides confidentiality and integrity of data/message.
- As a result of HTTPS, all the traffic between the client and server is encrypted. Even if the man in the middle captures all the traffic, he cannot decrypt the message nor manipulate it.
- Cain bypasses this by generating fake certificate from the legit certificate.The detailed process is explained here: http://www.oxid.it/ca_um/topics/apr-https.htm.
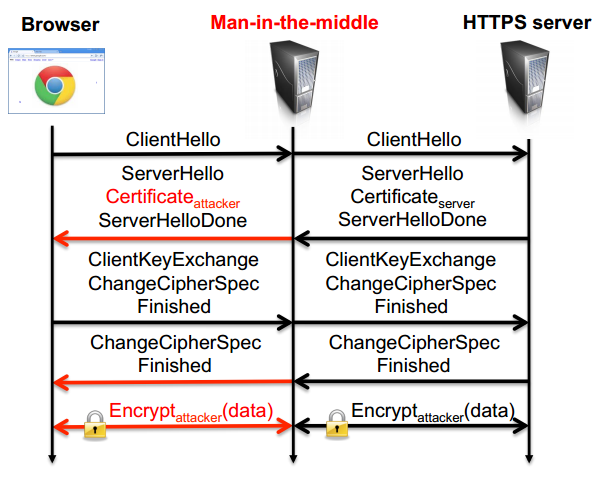
- Above image illustrates how a fake certificate can be used to bypass HTTPS. The man in the middle(Cain) generates a certificate with its own private key and sends it to the client. As a result the client think that the communication is secured through HTTPS, but the attacker can decrypt the message and sniff/modify plain text traffic.
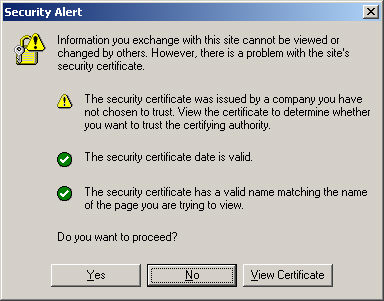
- However, one problem still exists with this method: the fake certificate created by Cain is not issued by the certificate authority. As a result a browser warns the user that the certificate is invalid. At this point, the attacker has to rely on user’s ignorance: user has to proceed even after reading the security alert.
7. Defenses
7.1 Password Protection
- As a user: Have strong passwords. A good password should satisfy these conditions -
- Not be a dictionary word, or a combination of them making it protected against dictionary attacks.
- Be long, so it would take a bruteforce attack many years to crack. A good length is generally 10+ characters, but it depends on what character set you are using. A 10 length numerical PIN can be cracked in around 2 seconds by a standard PC. A 10 length alphanumeric password with capitals and special symbols will take around 60 years to crack for a standard PC.
- Use a large character set. As demonstrated above, the characters comprising your password matter. Try to avoid common number and special symbols insertions however. Most people tend to increase the character set by capitalizing the first letter, replacing letters with similar looking numbers (like s to 5) and putting an exclamation sign at the end. Try to avoid doing this as most attackers will account for this (by modifying their mangling rules in a dictionary attack).
- Make the password memorable. If you make your password an impossible to remember 20 character assortment of gibberish, it is likely you will forget it or store it in an insecure way. Some people will do things like write their password down, or store it in a text file or e-mail, which defeats the purpose of having a strong password.
- Don’t reuse passwords. If it turns out a website was storing your password in plaintext and was hacked, it shouldn’t mean that all your other passwords like e-mail are compromised. Make sure to have different password for every service which needs a password.
This seems like a lot to keep track of. One recommendation is to use a password manager app like KeepPass. It automatically generates and securely stores passwords for all the services that you use. This can be dangerous however, as if an attacker can break into KeepPass they will have every single one of your passwords. So make sure to do research that determines whether your password manager is secure.
- Hash your passwords with a strong hashing algorithm. That means if the database of user credentials is stolen, the attackers won’t necessarily be able to access the accounts. Since weak hashes like MD5 are very easy to crack use a strong algorithm like SHA-512.
- Salt your passwords. Salting is essentially appending some sequence of characters to the password sent by the user before hashing it. By salting your passwords you are making bruteforcing harder, but also defeating rainbow tables. It defeats rainbow tables because even if the rainbow table finds a collision, it will be unable to input that as the password, due to the salt.
- Don’t use obvious names for fields. Avoid names like “password”,”id”, or “pass”. By making it difficult to discern what field contains the relevant information you are slowing down the attacker, as Cain and Abel will not be able to catch passwords from your website by default. This is however, security through obscurity so make sure it is not the only defense that you employ.
- Use and force HTTPS. As we’ve seen earlier HTTPS helps warn victims that they are possibly being ARP poisoned. If your website provides HTTPS make sure to force it, that is do not allow an HTTP connection even if it is requested and instead only allow HTTPS connection
7.2 Protection against ARP spoofing
- Use HTTPS whenever possible. It is not safe to pass sensitive information over plain HTTP. Do not trust sensitive information to websites that do not use HTTPS. Also, make sure that their certificate is valid and don’t ignore warnings that come up.
- Protect your network. ARP Spoofing does not work unless the attacker is connected to the network. So make sure that your network is not easily accessible, and don’t connect to networks with weak encryption. For example, don’t connect to networks that use WEP to secure it. In a similar vein, don’t connect to open networks as that would make ARP Poisoning easy for the attacker.
- Use APR Spoofing detection tools. One of the example of such tools is XArp. It detects when it is likely that you are under an ARP spoofing attack, and notifies you.
- Use a VPN. A VPN encrypts your connection and makes ARP Spoofing much harder, as the attacker has to decrypt your connection. Be warned however that this introduces the problem of which VPN to trust, as some have weak encryption and some can even sniff your connection maliciously.
- As a security professional:
- Use Static ARP entries. The way this works is every single computer on the network has a table of ARP entries they use and which cannot be updated by a simple ARP request, as the computers simply ignore them. This means that ARP Spoofing are mitigated as there’s no signal the attacker can send that could update the tables. The big problem with this is that it’s completely unscaleable. It does not work on any networks but the tiniest ones, and even then allowing a new user to connect is a hassle. This is because every time there is a change to be made (like a new computer connecting to the network) all the ARP tables have to be manually changed.
- Custom monitoring software. This is slightly similar to the static ARP entries, but more scaleable. A central server maintains a list of important ARP entries, like the file server, authentication server and so on. Otherwise ARP works exactly as it normally does. However, on a regular basis the computer’s ARP table is compared against the one maintained by a central server. If it does not match the system warns of an ARP spoofing attack and disregards the computers ARP table. This means that while ARP Poisoning can still happen between some hosts, the most important connections are maintained and monitored.
- Detection and blockade of ARP Spoofing attacks. Software like ARPWALL or even Wireshark can analyze packets to check for some signs of an ARP Poisoning attack. If it detects it, it notifies the user and blocks the offending connection.
8. Disadvantages of Cain and Abel.
- Can slow down the victims connection. This can potentially reveal the attack and make the user suspicious. In our tests we found around a 30% difference between a normal connection and an ARP poisoned connection but your results may vary. The added speed is due to the extra node the packets have to travel through.
- It cannot sniff passwords from many sites by default. Unless a site uses a password field like “pass” or “pw”, Cain and Abel will not detect it with the default configuration. The field has to be manually found and entered into the settings which is a hassle.
- Requires administrator privileges to run. This tool does not work unless you give it administrator rights, which means that you must own an administrator account on the computer to use it. This is different from some cracking tools like Ophcrack which do not require any account whatsoever to crack hashes.
- ARP Spoofing requires network access. As we’ve discussed before nothing can be done with ARP unless the user is properly connected to a network.
9. Demo
7.2 Decoder
7.2 Cracker
7.2 ARP
10. Sources
Password Algorithms: Internet Explorer 10 (Windows Vault)
http://en.wikipedia.org/wiki/Rainbow_table
Address Resolution Protocol (arp)
ARP Cache Poisoning
http://resources.infosecinstitute.com/password-cracking-using-cain-abel/
Introduction to ARP Poisoning Routing