Networking Basics
- See Notes from csc309
- Tutorial notes
- We also went through examples using firefox and parosproxy, nmap, wireshark, zenmap (well next time).
Footprinting/Fingerprinting
Definition: the gathering of information about a system or network (usually footprinting refers to the network, fingerprinting refers to system level information).
Attackerís point of view
- Identify potential target systems
- Identify which types of attacks may be useful on target systems
Defenderís point of view
- Vulnerability analysis:
Identify information youíre giving away.
Identify weaknesses in systems/network. THEN FIX THEM
- Know tools available to attacker
- May be able to tell if system is being footprinted, be more prepared for possible attack,
identify source of probe.
- Construct audit trail of activity
Information to Gather
System
- IP Address, Name and Domain
- Operating System: Type (Windows, Linux, Solaris), Version (98/NT/2000, Redhat 7/8/9,Fedora,SuSe)
- Usernames
- File structure
- Open Ports (what services/programs are running on the system)
- Physical Proximity/Location
Network
- System information for all hosts
- Network topology
- Gateways
- Firewalls
- Overall topology
- Network traffic information
- Specialized servers: Web, Database, FTP, Email, etc.
Linux tools
System
- uname -a: Determine system information, hostname, kernel version
- uptime: how long has the system been up
- hostname: Determine name of current system
- ifconfig: configure network interface. Displays
IPs and mac addresses for current system.
- who: Users on current system.
Useful for identifying unusual activity
(e.g. activity by newly created accounts or inactive accounts)
- last [-n] : Show last N users on system. Useful for identifying unusual activity in recent past.
- lsof: display currently open files, which process has them open and the processes owner.
- mount: show filesystem mounts
- ps aux: see all processes running and who owns them.
Network
- ping:
Potential Uses
- Is system online, through response.
- Gather name information, through DNS.
- Estimate relative physical location,
based on RTT (Round Trip Time) given in summary statistics
- Identify operating system: Based on TTL (packet Time To Live) on each packet line
TTL = number of hops allowed to get to system
64 is Linux default, 128 is Windows default (but can be changed!)
Notes: Uses ICMP packets. Often blocked on many hosts
- netstat:
Possible uses
- Shows connections, routing information, statistics
- find adjacent machines, used ports
Notes: Many flags
netstat // open sockets, etc.
netstat -s // summary statistics
netstat -r // routing tables
netstat -p // programs
netstat -l // listening sockets
netstat -ta
- traceroute:
Potential Uses
- Determine physical location of machine
- Gather network information (gateway, other internal systems)
- Find system thatís dropping your packets, evidence of a firewall
Notes: Can use UDP or ICMP packets. Results often limited by firewalls.
- finger localuser or finger@system or finger remoteuser@system
Potential Uses
- Collect usernames
- Determine if user is currently logged in
Notes: Often blocked
- nslookup, dig: associate domain name with ip and vice versa
Potential Uses
- Query internet name servers
- Find name for IP address, and vice versa
Notes:nslookup generally deprecated, generally use dig.
nslookup sometimes useful when dig fails
- arp: display the arp table. List machines that this machine has contacted recently.
Possible uses
- Useful to determine if a foreign system is on the network.
- Find adjacent systems
- whois or whois uw%.edu:
Potential Uses
- Queries nicname/whois servers for Internet registration information
- Can gather contacts, names, geographic information, servers,
useful for social engineering attacks
Port scanning
- nmap
Potential Uses
- determine the systems on the network (-sP) (example)
- determine the services they are running (-sT) (example))
- determine the version of services they are running (-sV)
For the defender, this is used to determine if unknown hosts are
on the system. If there are vulnerable services running on the network.
Packet sniffing
- ethereal/wireshark
Potential Uses
- Capture and view network traffic. Hacker can use this to capture cleartext
passwords. To view details behind uses of services.
Defender uses this to see if portscans are taking place, if unusual conversations
are taking place.
Intrusion Prevention
Linux Runlevels
General rule
- Don't run services you don't need.
- Don't run vulnerable versions of services you do need.
- Restrict who can use services.
Don't run services you don't need
- netstat: See which services are currently running on your system.
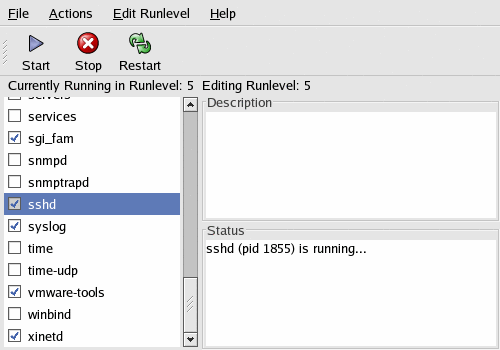
- runlevel editor: Used to add, remove services from a given runlevel. (bum/rcconf)
System Settings -> Server Settings -> Services
What you see below is a list of services that will all start
when the system enters runlevel 5.
- xinetd: use it's configuration files (in /etc/xinetd.d) to restrict, disable services run by this superserver.
In appropriate xinetd.d config file, set disable = yes if the service is not needed.
Don't run vulnerable versions of services you do need
- nessus: This tool automates nmap+understanding vulnerable versions of services.
- OpenVAS The world's most advanced Open Source vulnerability scanner and manager
Run this to report on versions of services running on a network.
Firewalling (Restrict who can use services)
Network Architecture
Intrusion Detection
Snort
is capable of
- real-time traffic analysis
- packet logging on IP networks
- protocol analysis
- content searching/matching
- detect a variety of attacks and probes , such as buffer overflows, stealth port scans, CGI attacks, SMB probes, OS fingerprinting attempts
Works by sniffing all traffic, understanding network protocols and patterns behind exploit attempts.
Guardian
Guardian is a security program which works in conjunction with Snort to automaticly update firewall rules based on alerts generated by Snort.
Low level attacks
Other tools
sectools.org

