Firewalling (Restrict who can use services)
Can be done at the
- Personal firewall level: firewall on my machine
- The Network Layer/packet filters: network firewall that looks at packets and who they are destined for, what ports they mention.
(from Wikipedia)
Network layer firewalls, also called packet filters, operate at a relatively low level of the TCP/IP protocol stack, not allowing packets to pass through the firewall unless they match the established rule set. The firewall administrator may define the rules; or default rules may apply. The term "packet filter" originated in the context of BSD operating systems.
Network layer firewalls generally fall into two sub-categories, stateful and stateless. Stateful firewalls maintain context about active sessions, and use that "state information" to speed packet processing. Any existing network connection can be described by several properties, including source and destination IP address, UDP or TCP ports, and the current stage of the connection's lifetime (including session initiation, handshaking, data transfer, or completion connection). If a packet does not match an existing connection, it will be evaluated according to the ruleset for new connections. If a packet matches an existing connection based on comparison with the firewall's state table, it will be allowed to pass without further processing.
Stateless firewalls require less memory, and can be faster for simple filters that require less time to filter than to look up a session. They may also be necessary for filtering stateless network protocols that have no concept of a session. However, they cannot make more complex decisions based on what stage communications between hosts have reached.
- Network Application Layer: Firewalls working at this level redirect and restrict based on payload data. They understand protocols such as smtp and http and are able to enforce rules based on this understanding.
- Application Level: Setup rules in the actual application to secure use of the system. For example, the Apache webserver, Postgresql database server, Postfix mail server each have their own security systems to
restrict the services they provide.
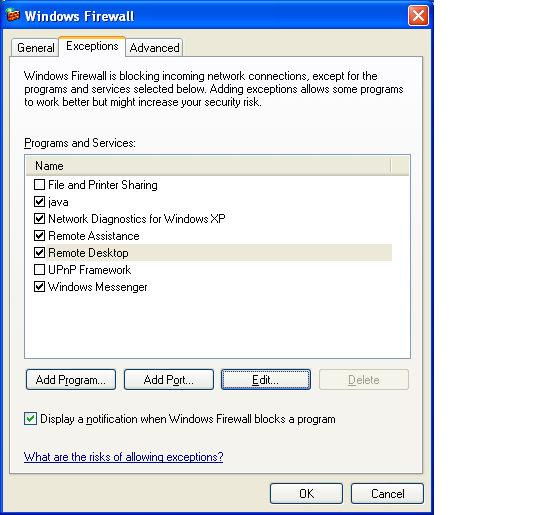
Personal Firewall
A simple firewall (running on the host in question) which
restricts the networks, hosts and domains that can access
services on the host in question.
Windows firewall is an example of this.
Network Layer: By example (iptables)
Private Side: VMNET8, 192.168.0.0/255.255.255.0
Ubuntu: 192.168.0.100
Serving web and mail to the private network
sudo bash for root
Backtrack3/5: IP (dhcp)
root/toor
Windows XP Pro: 192.168.0.33
csc347/password
DSL: 192.168.0.75 (To put this on the private network, you will need to switch to VMNET8)
Administrators machine
sudo su for root
Setup networking by DSL->Setup->Net Setup->netcardconf
Make the firewall the default gateway. Make sure you choose the
correct side of the firewall depending on where you put this on the network.
FC4 Firewall/Gateway:
eth1: 192.168.0.10
eth0: 10.10.10.10
root/password
see /etc/sysconfig/myFirewall.bash
Public Side: VMNET1, 10.10.10.0/255.255.255.0
RH72: 10.10.10.11
hacker/password
root/password
DSL: 10.10.10.128 (you can switch the IP of this machine manually)
DSL: 10.10.10.75
DSL: 10.10.10.33 (CEO)
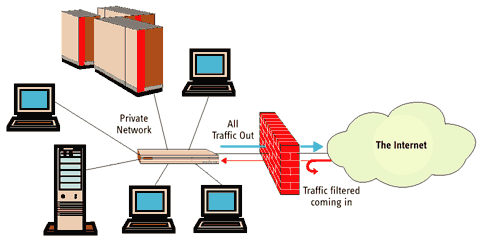 (from http://www.dmccormick.pwp.blueyonder.co.uk/coursecontent/09/9_04a.htm)
Like a personal firewall, except this firewall is considerably more powerful. It typically used
outside a specific system. Used to protect a network.
(from http://www.dmccormick.pwp.blueyonder.co.uk/coursecontent/09/9_04a.htm)
Like a personal firewall, except this firewall is considerably more powerful. It typically used
outside a specific system. Used to protect a network.
It can restrict, route and rewrite packets coming into the
firewall, going out of the firewall and those being routed through the firewall.
Decisions about packet rewriting and restricting can be made
based on packet source, destination and port.
At a high level, it is used to restrict access to services,
hide the network behind the firewall, act as a proxy
for services running behind the firewall.
iptables:
netfilter.org created iptables
and the associated framework to enable packet filtering,
network address [and port] translation (NA[P]T) and other packet mangling.
See This long tutorial!!
iptables consists of 3 basic tables:
- filter: used to determine which packets can be sent to, from and pass through this host
- nat: used to determine which packets have NAT and port translations applied
- mangle: used for other packet mangling
Each table consists of a collection of chains, filter has INPUT, FORWARD and OUTPUT.
Each chain has a list of rules mentioning a target.
For filter, targets include ACCEPT, DROP.
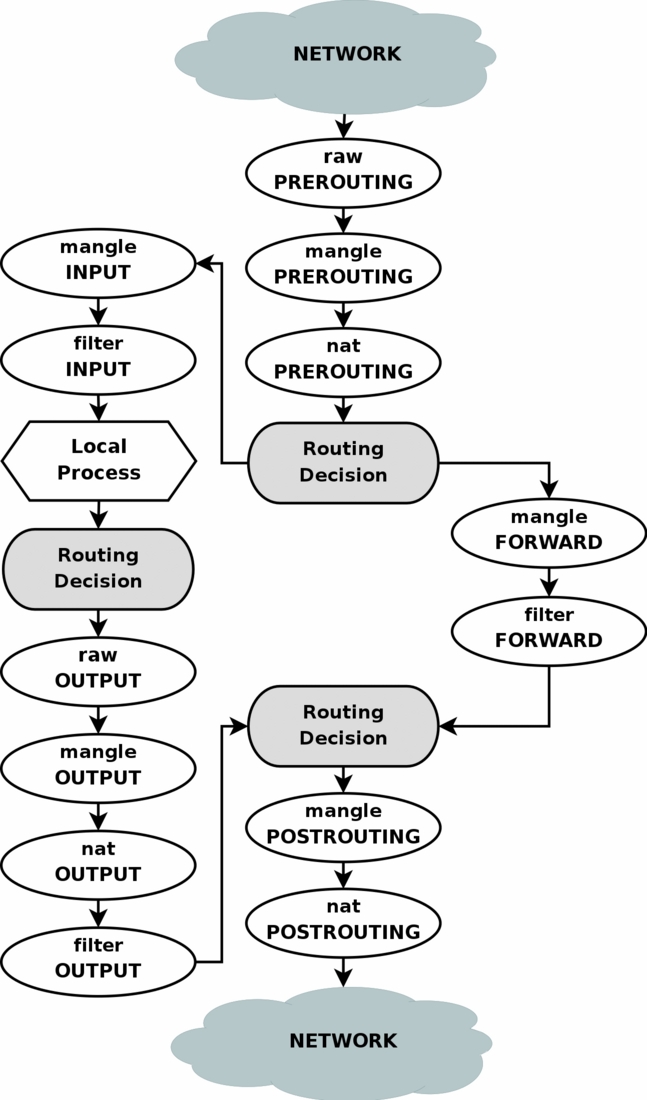 (from the iptables-tutorial)
(from the iptables-tutorial)
- filter table
- INPUT (chain)
- rule 1
- rule 2
- rule 3 ...
- default rule
- FORWARD (chain)
- rule 1
- rule 2
- rule 3 ...
- default rule
- OUTPUT (chain)
- rule 1
- rule 2
- rule 3 ...
- default rule
- nat table
- PREROUTING (chain)
- OUTPUT (chain)
- POSTROUTING (chain)
- mangle table
- PREROUTING (chain)
- OUTPUT (chain)
How packets are processed by the filter table... (from the packetfiltering-HOWTO)
_____
Incoming / \ Outgoing
-->[Routing ]--->|FORWARD|------->
[Decision] \_____/ ^
| |
v ____
___ / \
/ \ |OUTPUT|
|INPUT| \____/
\___/ ^
| |
----> Local Process -----
iptables example
#!/bin/sh
# flush all tables
/sbin/iptables -F
/sbin/iptables -t nat -F
/sbin/iptables -t mangle -F
# default policy ACCEPT
# /sbin/iptables -P INPUT ACCEPT
# /sbin/iptables -P OUTPUT ACCEPT
# /sbin/iptables -P FORWARD ACCEPT
# default policy (if none of the other policies match, apply these)
/sbin/iptables -P INPUT DROP
/sbin/iptables -P OUTPUT DROP
/sbin/iptables -P FORWARD DROP
# so we can talk to ourselves
/sbin/iptables -A INPUT -i lo -j ACCEPT
/sbin/iptables -A OUTPUT -o lo -j ACCEPT
# 192.168.1.39 is bad so don't allow them to ssh
# /sbin/iptables -A INPUT -s 192.168.1.39 -p tcp --dport 22 -j DROP
# 192.168.1.39 is bad so don't allow them to echo
# /sbin/iptables -A INPUT -s 192.168.1.39 -p tcp --dport 7 -j DROP
# 192.168.1.39 is bad, don't allow them to connecct
/sbin/iptables -A INPUT -s 192.168.1.39 -j DROP
# 192.168.1.39 is bad, don't allow us to connect to them
# /sbin/iptables -A OUTPUT -d 192.168.1.39 -j DROP
# so the local network can talk to us
/sbin/iptables -A INPUT -s 192.168.1.0/24 -j ACCEPT
/sbin/iptables -A OUTPUT -d 192.168.1.0/24 -j ACCEPT
iptables and NAT
From the NAT HOW-TO
- What is NAT (Network Address Translation)?
Rewrite packet source, destination, ports as they pass through the firewall
- Why do NAT? Share a single IP, hide your servers behind a firewall on a non-routable network, load sharing, transparent proxy
- Types of NAT
Source NAT (SNAT) and Destination NAT (DNAT).
Source NAT (SNAT) is when you alter the source address of the first packet: i.e. you are changing where the connection is coming from. Source NAT is always done post-routing, just before the packet goes out onto the wire. Masquerading is a specialized form of SNAT.
Destination NAT (DNAT) is when you alter the destination address of the first packet: i.e. you are changing where the connection is going to. Destination NAT is always done before routing, when the packet first comes off the wire. Port forwarding, load sharing, and transparent proxying are all forms of DNAT.
- How packets are processed by the NAT table (output ignored)
_____ _____
/ \ / \
PREROUTING -->[Routing ]----------------->POSTROUTING----->
\D-NAT/ [Decision] \S-NAT/
| ^
| |
| |
| |
| |
| |
| |
--------> Local Process ------
- SNAT
You want to do Source NAT; change the source address of connections to
something different. This is done in the POSTROUTING chain, just
before it is finally sent out; this is an important detail, since it
means that anything else on the Linux box itself (routing, packet
filtering) will see the packet unchanged. It also means that the `-o'
(outgoing interface) option can be used.
Source NAT is specified using `-j SNAT', and the `--to-source' option
specifies an IP address, a range of IP addresses, and an optional port
or range of ports (for UDP and TCP protocols only).
## Change source addresses to 1.2.3.4.
# iptables -t nat -A POSTROUTING -o eth0 -j SNAT --to 1.2.3.4
## Change source addresses to 1.2.3.4, 1.2.3.5 or 1.2.3.6
# iptables -t nat -A POSTROUTING -o eth0 -j SNAT --to 1.2.3.4-1.2.3.6
## Change source addresses to 1.2.3.4, ports 1-1023
# iptables -t nat -A POSTROUTING -p tcp -o eth0 -j SNAT --to 1.2.3.4:1-1023
- DNAT
This is done in the PREROUTING chain, just as the packet comes in;
this means that anything else on the Linux box itself (routing, packet
filtering) will see the packet going to its `real' destination. It
also means that the `-i' (incoming interface) option can be used.
Destination NAT is specified using `-j DNAT', and the `--to-
destination' option specifies an IP address, a range of IP addresses,
and an optional port or range of ports (for UDP and TCP protocols
only).
## Change destination addresses to 5.6.7.8
# iptables -t nat -A PREROUTING -i eth0 -j DNAT --to 5.6.7.8
## Change destination addresses to 5.6.7.8, 5.6.7.9 or 5.6.7.10.
# iptables -t nat -A PREROUTING -i eth0 -j DNAT --to 5.6.7.8-5.6.7.10
## Change destination addresses of web traffic to 5.6.7.8, port 8080.
# iptables -t nat -A PREROUTING -p tcp --dport 80 -i eth0 \
-j DNAT --to 5.6.7.8:8080
- Mixing NAT and Packet Filtering
You design your packet filtering completely ignoring any NAT you are doing. The sources and destinations seen by the packet filter will be the `real' sources and destinations. For example, if you are doing DNAT to send any connections to 1.2.3.4 port 80 through to 10.1.1.1 port 8080, the packet filter would see packets going to 10.1.1.1 port 8080 (the real destination), not 1.2.3.4 port 80. Similarly, you can ignore masquerading: packets will seem to come from their real internal IP addresses (say 10.1.1.1), and replies will seem to go back there.
In lecture, I went over this example, heading to this.
Network Application Layer Firewall
Firewalls that operate at this level actually understand
the protocols they are attached to. They watch the traffic
to ensure that communicating parties are actually using the
predefined protocol to communicate.
Example:
An firewall that watches port 80 (http) will ensure that
communicating parties are having an http conversation.
Application Level Firewall
The application (service) itself may allow the administrator to restrict when and
how the application is used. Note: Difference between this and above
is that Network Application Layer Firewalls operate independently of the
service they are firewalling. Network Application Layer Firewalls watch network
traffic. Application Level Firewalls have features dependent on the
particular creator of the service software.
Example: sendmail can restrict
who uses it and how it is used. It can restrict which domains can use it as a relay
(via /etc/hosts.allow and /etc/hosts.deny)
to prevent it from being used by spammers.
Example: xinetd (internet super server) is used to manage
a collection of services. It has configuration files which allow restriction
of how frequently a service can run, which domains/networks/hosts
can run the service etc. It supports logging of use of service.
# /etc/xinetd.conf
# Simple configuration file for xinetd
#
# Some defaults, and include /etc/xinetd.d/
# Logging to SYSLOG (/var/logs/secure in RH8 VM).
defaults
{
instances = 60
log_type = SYSLOG authpriv
log_on_success = HOST PID
log_on_failure = HOST
cps = 25 30
}
includedir /etc/xinetd.d
xinetd configuration for a particular service (echo)
# /etc/xinetd.d/echo
# default: off
# description: An xinetd internal service which echo's characters back to clients. \
# This is the tcp version.
service echo
{
type = INTERNAL
id = echo-stream
socket_type = stream
protocol = tcp
user = root
wait = no
disable = no
only_from = 127.0.0.1
only_from += 192.168.1.0
no_access = 192.168.1.33
}
You must restart the xinetd service after you have modified a service configuration.


 (from http://www.dmccormick.pwp.blueyonder.co.uk/coursecontent/09/9_04a.htm)
(from http://www.dmccormick.pwp.blueyonder.co.uk/coursecontent/09/9_04a.htm)
