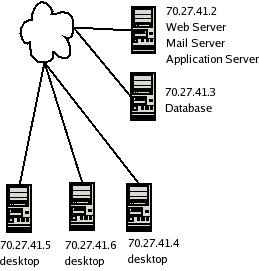
 Description:
Description:
- Each host has a public IP.
- The Web server is listening on port 80, Mail server on port 25, Application server on port 8080.
- The database server is listening on port 443, is only used by the application server
Vulnerabilities:
- All services on all systems vulnerable from external attack.
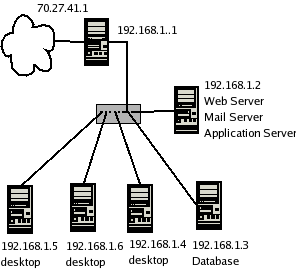 Description:
Description:
- 70.27.41.1 is the only public IP (this is the firewall)
- All other hosts have private (non-routable IPs).
- The firewall is forwarding ports 80, 8080 and 25 from the web to 192.168.1.2
- All other incoming connections are restricted.
- The firewall is running NAT for the network so that all internal systems can connect to the web.
Vulnerabilities:
- ports 80, 8080 and 25 are visible to the outside world (necessary)
if any of these services are compromised (so that 192.168.1.2 is compromised)
then the attacker will have direct access to the database and
all desktop systems.
- desktops (typically vulnerable) can see (and attack)
other servers.
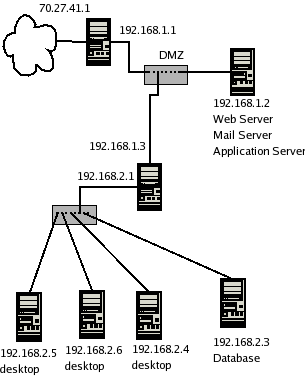 Description:
Description:
- As above, but this time we have created a Demilitarized zone
to protect the public servers from the internal systems.
- Note the introduction of a second filtering firewall at
192.168.1.3.
Vulnerabilities:
- desktops (typically vulnerable) can see (and attack)
other back office servers.
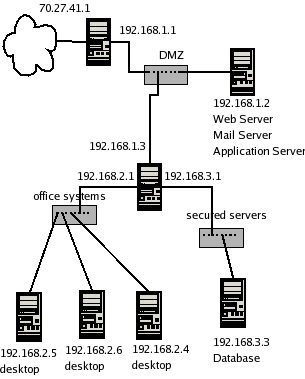 Description:
Description:
- As above, but this time we have added a third ethernet card
to the internal firewall. This allows us to protect internal
servers from internal desktop systems.
Vulnerabilities:




