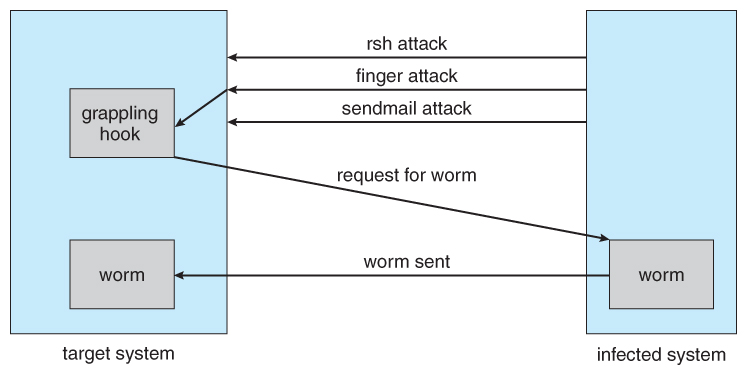
See The Morris Worm: A 15 Year Perspective (available on campus from IEEE Security & Privacy Magazine, volume 1 issue 5)
A brief summary can be found here
or see Communications of the ACM (CACM) Vol. 32, No. 6, June 1989 , The Worm Story
Executive Summary:
This update resolves a newly-discovered, privately reported vulnerability. A buffer overrun vulnerability exists in the processing of JPEG image formats that could allow remote code execution on an affected system. The vulnerability is documented in this bulletin in its own section.
If a user is logged on with administrator privileges, an attacker who successfully exploited this vulnerability could take complete control of an affected system, including installing programs; viewing, changing, or deleting data; or creating new accounts with full privileges. Users whose accounts are configured to have fewer privileges on the system would be at less risk than users who operate with administrative privileges.
Microsoft recommends that customers apply the update immediately.
